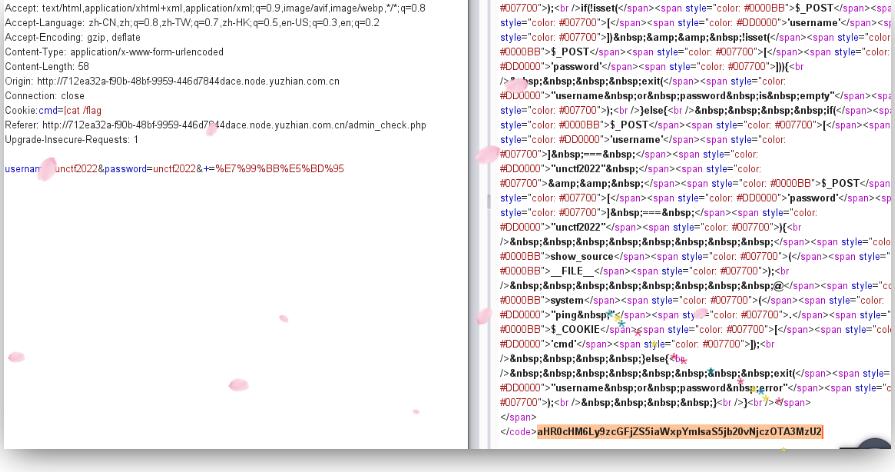
rank:3Crypto
这是什么古典玩意
第一部分 先base64解码 IJWHKZKTNBQXE2Y= base32 解密 BlueShark
第二部分 先用十六进制转化为Unicode码 \u53\u65\u65\u6D\u73\u53\u3 然后转化为字符 SeemsS0
第三部分 猪圈密码 cute
然后连在一起就是flag
ISCTF{BlueShark_SeemsS0_cute}
呜呜呜我的md5脏了
I{i?8Sms??Cd_1?T51??F_1?}
由所给的这个字符串判断应该先进行栅栏解密当key=5的时候得到
ISCTF{md5_is_11??1??8???}
然后进行脚本解密
脚本如下
import hashlib
c = 'ISCTF{md5_is_11??1??8???}'
m = '88875458bdd87af5dd2e3c750e534741'
for i in '1234567890':
c1 = c.replace('?',i,1)
for j in '1234567890':
c2 = c1.replace('?',j,1)
for p in '1234567890':
c3 = c2.replace('?', p, 1)
for q in '1234567890':
c4 = c3.replace('?', q, 1)
for a in '1234567890':
c5 = c4.replace('?', a, 1)
for b in '1234567890':
c6 = c5.replace('?', b, 1)
for d in '1234567890':
c7 = c6.replace('?', d, 1)
s = hashlib.md5()
s.update(c7.encode('utf-8'))
flag =s.hexdigest()
if flag == m:
print(c7)
#ISCTF{md5_is_11451438324}咦 这个密码 怎么怪怪的
JVAB6NR=
FCFOQCB=
JG6NSTP=
UPM4BGU=
GN3VKM==
题目给了这五段base编码后的字符串,分别base解密后得到的不是正确结果
然后感觉是栅栏密码分组后的
然后先还原JFJUGVCGPNAF6M3BON4V6QSBKNCTGMRBPU======
然后base32解码得
ISCTF{@_3asy_BASE32!}
ezcry
已知n,c,seek1,seek2,seek3只需求得p,q就可以求得flag
先尝试用方程组求得p,q,s,k但是有4个未知数,但是只能列出三个方程
然后发现seek3可以分解 分解之后就很容易求出p,q了
然后列两个方程求出p,q然后求出flag
脚本如下:
import sympy
import gmpy2
import libnum
e = 65537
n = 17034526359906374675222899048129793386473729727961851733668266173715506273934226618903915327347680201386438684211280871430960401386916021458749533875225149368757915582850037170031336862864220965224712317292408675261654733853726119671544885158743864358155418727967683788352892259519172776767011253307992508658787036093010953540438865556151687132667690293590304094069132122821611257522409132491206241878258953750975043892338280574703622715614385904469190033441247428911800257097240824225432194243602777112774675510936575635571170740329720227162079500469956310746873132644419840611848333802207608652869080821316814006039
seek1 = 31064534580137722018723185060822560614595271317101024671103834301982025703308358280617670492170754990183711198694392500995348706299728134379707212369534471489902209545060592051514886997951859233729914969365008090709174580598044945031296428531946547802954873288796478626936584991410702713951383782424003825610226728036611739090258953115031673157531
seek2 = 24213197274140919663950771475506320265583015671558310318006684746019240494812396672068641326932339831508586851960432536051863105773343184877340119017546817780287117748145293115469964769795237573829418533841547969451268532899237529671580701722254679851009751345719473395857872899046537572034595080443184983155696803469587776652323407147950333716539
# seek3 = 44155715757886274586781970607943060213741487009882893164192666734219021562031
k = 176868710737612660790124725586933365207
s = 249652499719930280463165749259207398633
c = 6636871845889289821451339461667353441602430792099749101933216934629214305159040913567522609116395485018234259025910227221402350884391969711051377864656945164699379734982178962637190192088596776288873871651609167259167456816094141938735498585327839045360319836147041837569528592447701501104067430848582239927052031661696213986982946173792468753773505681630323945625892041031455025095934790620541499679023777086690062211807019645557781380979957862910047981754126193036968611612056475750787560328372643151874535031184052794483578557248028165948247504989100884012688908781349748818365779371062209169311607720595792421590
p = sympy.Symbol('p')
q = sympy.Symbol('q')
f1 =p*s - seek1
f2 = q*k - seek2
result = sympy.solve([f1,f2],[p,q])
print(result)
# p = result[0][0]
# q = result[0][1]
p = 124431097685731585500751867561577386168625841833110547803689338621205694806894593800890539870901241604771309656881714338980632734600555998963734012020140199718421450936912672638698198874438316460684901133302344433574864927296261487308172012685704080591703927800706930307570111656989099386334418808318738228707
q = 136899269368574494181432774464678202037635589190950946226297544277459575545677315054120424232811345008456618479471930375486284959459949992475679011596136875096300441920570897559993673334614086077512235940271412778240309588973215899038656984058786224113488739164322245715370193417530133818250200774863603490877
print(p)
print(q)
phi = (p-1)*(q-1)
d = gmpy2.invert(e,int(phi))
m = pow(c,d,n)
print(libnum.n2s(int(m)))
#ISCTF{iiii|||yesyes||7777}babyrsa
已知e,phi,c
可以先直接求出d
然后需要求p,q
由于p,q是相邻的两个素数 可以根据先对phi开平方
r = gmpy2.iroot(phi,2)
然后求出r后面的一个素数记为q 然后根据phi列方程求出 p
然后求出n
然后即得flag
import gmpy2
import libnum
import sympy
e = 0x10001
phi = 11998145197184838105291668748328177280207361667546370722759758550200386112478801305683579153942751165452647656673385449297455560085865712968985383490367475984832103238596934094135353170257339614559178443729484992289380330326343473326373076256926770972074683466001586625109364413771716300886242679064050279982192814946404692347546718488456485946902248120569680365122714051066115263800073280766317934165938044443605816890762489369759667593014079143278938847700684310154017484382180324831332527966465023501690149664921975200082428884572496102388046780321762496321487913829155767534947229165886644311869593584303424397016
# r = 109536045196021378473484632066472150683521336347358874526866331690092816367179030745104763602807576505784282588391579330792050561206606208658316946611185794570291516186946574151436992714139093506271221446818524824573954054758828492925882010545627804144648642873153564353555136207966912120214314518375212161620
c = 5664235030100231880171042228110930207351619841860785495929861788749956436657598539033166266920085041056539484368799525891006461921744810454002229224070342640529484554920046100814190479604751667796353636578589439575896923937945959721385425716210546145718343511555866077148390467362495462929359632111674082222918151696522137240478900570056689827712787018876034334301771868147820786419006234529563416734953393480238739362002713175495890402512002469332947145115452344040709333447223824491510840788018172189866931550385951940611161143400804317944263940630025758568750312753125034413169961147691163044924934280636235493483
d = gmpy2.invert(e,phi)
print(gmpy2.iroot(phi,2)) #先把phi开方求得r然后求r后面的一个素数 即为 q然后 在列方程求出 p
q = 109536045196021378473484632066472150683521336347358874526866331690092816367179030745104763602807576505784282588391579330792050561206606208658316946611185794570291516186946574151436992714139093506271221446818524824573954054758828492925882010545627804144648642873153564353555136207966912120214314518375212162597
p = 109536045196021378473484632066472150683521336347358874526866331690092816367179030745104763602807576505784282588391579330792050561206606208658316946611185794570291516186946574151436992714139093506271221446818524824573954054758828492925882010545627804144648642873153564353555136207966912120214314518375212160647
# p = sympy.Symbol('p')
# q = gmpy2.next_prime(r)
print(q)
f1 = (p-1)*(q-1)-phi
result=sympy.solve(f1,p)
print(result)
m = pow(c,d,p*q)
print((p-1)*(q-1))
print(libnum.n2s(int(m)))
blueshark{ISctf_i4_interest1ng}blueshark{ISctf_i4_interest1ng}
韩信点兵
根据所给源代码亿以及所给的输出的文件
第一行应该是第一个字母经过源代码的变换得到的
盲猜前五个字母应该是 ISCTF
然后写脚本爆破key
#先爆破k 由给的附件得应该是每一行代表一个字母 第一个字母应该是 I
#然后用第二个字母爆破k得到的还是 63311
#第三个爆破出来也是63311
p1 = 60719
p2 = 41941
for key in range(pow(2,17)):
i = (((ord('I') << 4) & 0xff) + ((ord('I') >> 4) & 0xff)) ^ key
if i%p1 == 2732 and i%p2 == 21510:
print(key)
#KEY = 63311然后根据中国剩余定理可以求出经过第一次变换后的字符
from functools import reduce
def CRT(mi, ai):
# mi,ai分别表示模数和取模后的值,都为列表结构
# Chinese Remainder Theorem
assert (isinstance(mi, list) and isinstance(ai, list))
M = reduce(lambda x, y: x * y, mi)
ai_ti_Mi = [a * (M // m) * gmpy2.invert(M // m, m) for (m, a) in zip(mi, ai)]
return reduce(lambda x, y: x + y, ai_ti_Mi) % M然后爆破还原
for j in '1234567890abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ{!@#}?$%^&*()-=\<>/':
if wp == (((ord(j)<<4)&0xff) + ((ord(j)>>4)&0xff))^key:
print(j,end='')然后写成一个脚本
import gmpy2
from functools import reduce
def CRT(mi, ai):
# mi,ai分别表示模数和取模后的值,都为列表结构
# Chinese Remainder Theorem
assert (isinstance(mi, list) and isinstance(ai, list))
M = reduce(lambda x, y: x * y, mi)
ai_ti_Mi = [a * (M // m) * gmpy2.invert(M // m, m) for (m, a) in zip(mi, ai)]
return reduce(lambda x, y: x + y, ai_ti_Mi) % M
key = 63311
mi = [2732 ,21510] #后两列数据
ai = [60719 ,41941] #前两列数据
m = CRT(ai,mi)
for j in '1234567890abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ{!@#}?$%^&*()-=\<>/':
if m == (((ord(j)<<4)&0xff) + ((ord(j)>>4)&0xff))^key:
print(j,end='')
然后每次运行换成下一行的数据 最后连起来得
ISCTF{6e0f1ad4-96a6-4b77-867d-0c69cb7ad019}
ezRSA
根据题目得这是一个典型的phi和n不互素问题直接套用脚本
import gmpy2
from Crypto.Util.number import *
# 当e约去公约数后与phi互素
def decrypt(p, q, e, c):
n = p * q
phi = (p - 1) * (q - 1)
t = gmpy2.gcd(e, phi)
d = gmpy2.invert(e // t, phi)
m = pow(c, d, n)
print(m)
msg = gmpy2.iroot(m, t)
print(msg)
if msg[1]:
print(long_to_bytes(msg[0]))
p = 146061540583135242741006647792481468215928177245453689591382075771990192360040412020479342624228118794110240955451899373848827328177557126556072570082923983968091404980923313006963667391261364191537502509633623502033578910844508808321175673461956149400289968262858691371016246515264343715246136003074155184273
q = 106988826778655284666865642844938578070029566283623778317110345394696520999319699165122638213405544697509248818119744714371964212582672270467711234178627339558783803718844973937701655329775612593193896887658613019039808270266901149871250769922857432588126510259997039777751047281603319139760808677732919216899
e = 740
c = 6282526058961246581872664236584053247822096703448673698014149841099601111078858783085447440545491467659016466697346055841162217815656467685468263870813754625318960798390457353869689600971254126026498299128586642169553158659216998193596000256435504143502966206895545701691216757482393700125791878031903647831939512035110314068235625347074791191183719857770670134500097347113475463330210378392860796906074883251200522628116993249459465350593837432195675595929482809838619649519612607292091411530134831844063986714485104831320923176335931609571205307034732956741442770883207107022828296237748601658720079333177460160664
decrypt(p, q, e, c)
ISCTF{1dedc976-d253-4053-b2f5-557282f41fc5}
蓝鲨密码
先ook解码得到一串十六进制的字符
67414E6C686C6438676C396267414E6C686C6438676C396238356438676C39626B5178316B414A326A356C35383439636C6B6B776B5178316B4149776B5178316B414A6A69343569695139636C6B6C326A356C356B5178316B414A326A356C35383439636C6B6C6A6934356969526438676C39626B5178316B4149776B5178316B414A326A356C3567414E6C686B39636C6B6C326A356C3538356438676C39626B5178316B414A326A356C3538356438676C396238356438676C39626B5178316B414A6A69343569694F316A6934356969526438676C39626B5178316B414A6A69343569694F316A69343569695139636C6B6B776B5178316B414A326A356C356B5178316B41497767414E6C686C6438676C396267414E6C6869316A6934356969526438676C3962383439636C6B6C6A69343569694F316A6934356969526438676C396267414E6C686C6438676C3962383439636C6B6C326A356C3567414E6C686B39636C6B6C326A356C35
然后16进制转为字符得
gANlhld8gl9bgANlhld8gl9b85d8gl9bkQx1kAJ2j5l5849clkkwkQx1kAIwkQx1kAJji45iiQ9clkl2j5l5kQx1kAJ2j5l5849clklji45iiRd8gl9bkQx1kAIwkQx1kAJ2j5l5gANlhk9clkl2j5l585d8gl9bkQx1kAJ2j5l585d8gl9b85d8gl9bkQx1kAJji45iiO1ji45iiRd8gl9bkQx1kAJji45iiO1ji45iiQ9clkkwkQx1kAJ2j5l5kQx1kAIwgANlhld8gl9bgANlhi1ji45iiRd8gl9b849clklji45iiO1ji45iiRd8gl9bgANlhld8gl9b849clkl2j5l5gANlhk9clkl2j5l5然后用base64解码但是默认的基本字母表是 A-Za-z0-9+/= 但是不太行 试了其他密码也解密不成功 又回来想了一下base64 改变一下基础字母表的顺序
直到试到 0-9a-zA-Z+/=为字母表得到flag
上脚本
import base64
str_1 = "gANlhld8gl9bgANlhld8gl9b85d8gl9bkQx1kAJ2j5l5849clkkwkQx1kAIwkQx1kAJji45iiQ9clkl2j5l5kQx1kAJ2j5l5849clklji45iiRd8gl9bkQx1kAIwkQx1kAJ2j5l5gANlhk9clkl2j5l585d8gl9bkQx1kAJ2j5l585d8gl9b85d8gl9bkQx1kAJji45iiO1ji45iiRd8gl9bkQx1kAJji45iiO1ji45iiQ9clkkwkQx1kAJ2j5l5kQx1kAIwgANlhld8gl9bgANlhi1ji45iiRd8gl9b849clklji45iiO1ji45iiRd8gl9bgANlhld8gl9b849clkl2j5l5gANlhk9clkl2j5l5"
str_base = "0123456789abcdofghijk1mnepqrstuvwxyzABCDEFGHIJKLMN0PQRSTUVWXYZ+/"
str_zh_base = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
flag = base64.b64decode(str_1.translate(str.maketrans(str_base,str_zh_base)))
print(flag)BLUESHARKBLUESHARK SHARKSHARKBLUE BLUE SHARK SHARKSHARKBLUEBLUESHARKBLUE BLUESHARKSHARKSHARK SHARKBLUEBLUEBLUEBLUE SHARKSHARKBLUE SHARK SHARKSHARKSHARK SHARKSHARKSHARKSHARK SHARKBLUE SHARKBLUESHARK BLUESHARKBLUE SHARKSHARK BLUESHARK SHARKSHARKBLUESHARK BLUEBLUEBLUEBLUEBLUE
得到这样的一串字符 明显的二进制形式
转化为二进制得
根据尝试 BLUE代表1 SHARK代表 0
1010 001 1 0 001101 1000 01111 001 0 000 0000 01 010 101 00 10 0010 11111二进制没有解出来东西 看到其中带空格 想到摩丝密码
试一下摩斯密码
-.-. ..- - . ..–.- -… .—- ..- . … …. .- .-. -.- .. -. ..-. —–
CUTE_B1UESHARKINF0
提交发生大写不对转化为小写试一下
ISCTF{cute_b1uesharkinf0}
easy_AES
本来是用base64在线网站解密结果什么都出不来 然后利用了base集成工具解密得到是字节流
第一个解密结果
b'\x00\x07\n\x00\x0f//8(3\x16:& \x16\x1c,&,)i\x07<7*1:ui\x15\x0c\x07i?,-i=:t\x07!0;(<e\x1d\x1fi\x7fc\x7fa~`\x7fb\x7f7\x7fe\x7fc'
第二个解密结果
b'\x14\xe6\xb9h\xb0cz\xe2\n\x00Zr\xf1\xe2\xe4M\xbeU\x93\xc7\xc8\xbd\xcf\x10\xb8\xca\x0b\x1e3A\xfd\xf7'
然后根据hint第一个是异或加密后得密文 第二个是aes加密后的密文
所以应该是AES_CBC模式 需要求出key和iv
由于key一般是重复的 可以先求出重复的字节
m1 = b'\x00\x07\n\x00\x0f//8(3\x16:& \x16\x1c,&,)i\x07<7*1:ui\x15\x0c\x07i?,-i=:t\x07!0;(<e\x1d\x1fi\x7fc\x7fa~`\x7fb\x7f7\x7fe\x7fc'
c = list(m1)
a = "ISCTF"
b=[]
for i in a: #把ISCTF转化为对应的ASCII码值
b.append(ord(i))
for i in range(len(b)):
c1 = b[i] ^ c[i]
print(chr(c1), end='')
#得到 ITITI
#所以key 是以I T 重复的
然后把key填充的和m1一样长 在和m1进行异或 然后输出
m1 = b'\x00\x07\n\x00\x0f//8(3\x16:& \x16\x1c,&,)i\x07<7*1:ui\x15\x0c\x07i?,-i=:t\x07!0;(<e\x1d\x1fi\x7fc\x7fa~`\x7fb\x7f7\x7fe\x7fc'
c = list(m1)
key = ''
for j in range(len(c) // 2):
key += 'IT'
# print(key)
d=[]
for i in key: #把key转化为对应的ASCII码值
d.append(ord(i))
c1 = ''
for i in range(len(c)):
a = chr(d[i] ^ c[i]) # key和m1进行异或
c1 = ''.join(a)
print(c1, end='')
#AES key is Nuyoah,IV=676574666c6167
from Crypto.Cipher import AES
from Crypto.Util.number import*
def pad(c):
l = len(c)
flag = l % 16
if flag != 0:
add = 16 - (l % 16)
c = c + ('\0' * add).encode('utf-8')
return c
m = b'\x14\xe6\xb9h\xb0cz\xe2\n\x00Zr\xf1\xe2\xe4M\xbeU\x93\xc7\xc8\xbd\xcf\x10\xb8\xca\x0b\x1e3A\xfd\xf7'
key = b'Nuyoah'
iv = 0x676574666c6167
iv = long_to_bytes(iv)
key = pad(key)
iv = pad(iv)
aes = AES.new(key,AES.MODE_CBC,iv)
flag = aes.decrypt(m)
print(flag)
得到 flag ISCTF{Yu_SI00_JIngY4uan@66!}本来是用base64在线网站解密结果什么都出不来 然后利用了base集成工具解密得到是字节流
第一个解密结果
b'\x00\x07\n\x00\x0f//8(3\x16:& \x16\x1c,&,)i\x07<7*1:ui\x15\x0c\x07i?,-i=:t\x07!0;(<e\x1d\x1fi\x7fc\x7fa~`\x7fb\x7f7\x7fe\x7fc'第二个解密结果
b'\x14\xe6\xb9h\xb0cz\xe2\n\x00Zr\xf1\xe2\xe4M\xbeU\x93\xc7\xc8\xbd\xcf\x10\xb8\xca\x0b\x1e3A\xfd\xf7'然后根据hint第一个是异或加密后得密文 第二个是aes加密后的密文
所以应该是AES_CBC模式 需要求出key和iv
由于key一般是重复的 可以先求出重复的字节
m1 = b'\x00\x07\n\x00\x0f//8(3\x16:& \x16\x1c,&,)i\x07<7*1:ui\x15\x0c\x07i?,-i=:t\x07!0;(<e\x1d\x1fi\x7fc\x7fa~`\x7fb\x7f7\x7fe\x7fc'
c = list(m1)
a = "ISCTF"
b=[]
for i in a: #把ISCTF转化为对应的ASCII码值
b.append(ord(i))
for i in range(len(b)):
c1 = b[i] ^ c[i]
print(chr(c1), end='')
#得到 ITITI
#所以key 是以I T 重复的然后把key填充的和m1一样长 在和m1进行异或 然后输出
m1 = b'\x00\x07\n\x00\x0f//8(3\x16:& \x16\x1c,&,)i\x07<7*1:ui\x15\x0c\x07i?,-i=:t\x07!0;(<e\x1d\x1fi\x7fc\x7fa~`\x7fb\x7f7\x7fe\x7fc'
c = list(m1)
key = ''
for j in range(len(c) // 2):
key += 'IT'
# print(key)
d=[]
for i in key: #把key转化为对应的ASCII码值
d.append(ord(i))
c1 = ''
for i in range(len(c)):
a = chr(d[i] ^ c[i]) # key和m1进行异或
c1 = ''.join(a)
print(c1, end='')
#AES key is Nuyoah,IV=676574666c6167from Crypto.Cipher import AES
from Crypto.Util.number import*
def pad(c):
l = len(c)
flag = l % 16
if flag != 0:
add = 16 - (l % 16)
c = c + ('\0' * add).encode('utf-8')
return c
m = b'\x14\xe6\xb9h\xb0cz\xe2\n\x00Zr\xf1\xe2\xe4M\xbeU\x93\xc7\xc8\xbd\xcf\x10\xb8\xca\x0b\x1e3A\xfd\xf7'
key = b'Nuyoah'
iv = 0x676574666c6167
iv = long_to_bytes(iv)
key = pad(key)
iv = pad(iv)
aes = AES.new(key,AES.MODE_CBC,iv)
flag = aes.decrypt(m)
print(flag)ISCTF{Yu_SI00_JIngY4uan@66!}
ezzzzzzzzzzzzzzzzzlattice
本来想通过所给的式子求出m但是所给的已知量很有限
c = (inverse(e, q) * useful + pow(m, e, q)) % p根据题目提示和题目源码应该是先构造一个格
#sage
q = 1315983632487139089617750670154806119268275210512095786866484175281321006406573324366047625051972678757
c = 60387115272108048744163258178807978405325618700171846384705851810106837854037850805257374685113348413056577421691682675686001837494490048119950328531119497762814869873825424704659636533573270470954454941469406739721475906819952069839004328782107324171279028483963429998937448889397109790478764402609376506913
useful = 162370170072252258856710656455811686368377830683038717890206663789692454074011190117398852659489809988489952239866676742924352883793663553325742572975946454543375668892992992200624019014742120485443782570890632500244797827950741064652268324028847648386398711812294242276270652020603354038915302515758254440951
v1 = vector(ZZ, [1, 0,-useful])
v2 = vector(ZZ, [0,1, c])
v3 = vector(ZZ, [0,0,p])
s = matrix([v1,v2,v3])
# 利用LLL算法
shortest_vector = s.LLL()[0]
print(shortest_vector)(375283327991706527645892100994438033485659744645186444913417551360585656230580960050994092510744912156, 1, 1302776248491245050044169675895743333702637313328702788561323578316558548494899852273477813698856258236)e的逆等于第一个数字
pow(m, e, q)等于第二数字
然后爆破出m
for i in range(10):
m=pow(c1,d,q)+i*q
m=libnum.n2s(int(m))
print(m)
if b'ISCTF{' in m:
print(m)
break总的脚本为
import gmpy2
import libnum
q = 1315983632487139089617750670154806119268275210512095786866484175281321006406573324366047625051972678757
c = 60387115272108048744163258178807978405325618700171846384705851810106837854037850805257374685113348413056577421691682675686001837494490048119950328531119497762814869873825424704659636533573270470954454941469406739721475906819952069839004328782107324171279028483963429998937448889397109790478764402609376506913
useful = 162370170072252258856710656455811686368377830683038717890206663789692454074011190117398852659489809988489952239866676742924352883793663553325742572975946454543375668892992992200624019014742120485443782570890632500244797827950741064652268324028847648386398711812294242276270652020603354038915302515758254440951
e0 = 375283327991706527645892100994438033485659744645186444913417551360585656230580960050994092510744912156
c0 = 1302776248491245050044169675895743333702637313328702788561323578316558548494899852273477813698856258236
e=gmpy2.invert(e1,q)
d=gmpy2.invert(e0,q-1)
for i in range(10):
m=pow(c0,d,q)+i*q
m=libnum.n2s(int(m))
print(m)
if b'ISCTF{' in m:
print(m)
breakISCTF{37f80ae2-5142-4f9b-827c-1620514e4030}
Misc
酱紫乱
写出脚本把所有文件读取 然后发现是base64编码 然后直接解码得到
IIL{oLSuI{_33LFCS3LLrrII{TuCSs_{FIIosTr7s_{3FuLu{3I7su{SuTcsrtL_tC_SsCIS{FtcCTc_cL3o{t7ICcor7uLTFc7{3LIcoC37TIsTtcT7otcLF{Io7u73ScoIs3crosTuSTIS_F3sF_{CoS{tsIFrLroCT__tsCocSCo{ISIrsoFcu_L{7C3IS_S_tTuSIc7uFLFC{3rIs_o7cut{tuoc_cTtrLTtSSICcooFI_CocrSLScC_L_ooI__u7T{sT_rFT7Fto3{uL77u3IoT__{3o{CItuLsc_sLTouotrF3S3r{3srtFC{7CLItuS_I_{s_ctoLcsFC77cTcLrSusIo3rILCo{77CrCuFL7r{ouIcsu{_7cFct33troIIrCt7CTSou_Sc7tCusL3Ts{touSCF3SoT{C7C_SSSorFTFS{FtssorI{I{7{3C{sTrutL_Cr7Fr3s7TFT3Stcrst_cs{uLsoIoLT3ScIsFFSFTTrFucTcuI{L33_CStoCTroCrIIL_ucTITCttCFtCrS_rruCoSS7T_IuLs_T_S3cS{r3I{Ito7tuuo33{IrscSr{IIco7STSstLS7SuFSLIs7oF7_Cr7FuFtt{uLSF{TSrTTT_SSuStF{I3CC3oI3srtCs7CLC_cFTccSLFFSCs_uTFCILT3_C_73L3cLSTS7r3{{so{TSS{F7CSr{SoCLSFc_ccTT3L3F3FsosC__c7C_SLCuoSs{CoTISuS{3F{S3IFT7{_LFCItt_toFCuuo73S{cFTcLT7oFLtoFICu__ucLTS3CcoSFITL{srrscuCo_Lcss7o_F3cI{7CTtcrur3SsostL7SFr{oS_FIrLT{IF73cTs_ooIcFTCsLscSrLru{LruL_CTF3LuC{c{CI_FC77C{3ott3CtCSFoCFCu7cITT7ILoCto_s{TIF3s_IF{LTctCo7STS_IIFSu_L3SC{{7totoSSsusT{ou7CtI7{srFtF{cF3I{uCs33SFCsF7{surcTr{SL_{C{s33tu__TsI7F7Io3u{sFII{_cSS_soLcFISTS_FrToITcToLLuss{{ocoIC337oo7CrIsT7cFTusoorLTT{rcSIC{IsFLCFC_SS{{_3IouscISScTC{rttSC3tFu_S37u{tCIos_{TLc_ICCs7oLCco3IoIFLctLtIu3r{{s3ust7o_uFT3CT_7rCcuFT{rFsFS_u_TCoooLcCFFcuuo_cSTtIcFT77oss__TL7uLo37CI_ucF_Fc3rI7urTTrs_T37oF_LIu33LC{7TFrCCSus3oFIc7_3{7LLtLtSTIF{C7s_rIC{STt_ttC3s{I{TCSL_{LLuoC3{SLTLu7c7uIc_I{TSSucI_LFSScT{FsT3ILtLcF3_7Csc_7c_LcI_{TcFtC3{o7T7TL_FSot3rFTS_Iu_SICtosr3o_crLrF_c3rTss{_IrtSFFtCsc{S_TL{T{TtcIucCCLIoItotLo_oCFo{CoSoCccCrorS7toC{oCtSoc33rsCouSTuCT3uL7Ict7rr{3LosC_uTIssLL{SLLFTo{7LTIoI{_cs7osrSCcLSs7CSL{SL7L7{uo_{cuut3Lc{LL}rcF73{{CstTsIIsS_Lts{FCStFFIs7tITS7S_uCCSuT_c{373sL7rcLtTL7C3SoSuI_73Is7sTIcTII7CsuF3c_FIt3sTtFsSrLLFtFtstF_{tSTrSToS{_FI{77Lu7usSuSsCo7ctTcFt{{FrTsso_C{FFLtocICr7FTrr3ouTsSTt_ccLr{_ITLIL{7tTrusIIrcCI_IItoscISTFL{LS{TtcSt_CS3sr_tICcSotI3sFcFSu_{stIuCtCr{TTFF7FT3_F{u3_CFCrFuFFo_TSuLto_SCTt{I_tTo7oIosTur7{stuLcrCIssttFc{LSTcS_7FutFC{rtTsFT7ccscCILI_CS7L3uIsSIFcctcutsr3SsTrSuc3cssIuTuTsoC3rscSru{cTrsSS{tT3ITI7csL33{ccC_7rF_7_ocrLIur7{tC3_urCIL_FL_sLuo7coFo_u37FTco{_sTF7ssIsuI_uosSou{CII{r_IssI3_rL{TosSor_CoC{tssCtL{TSSu_TLFCFLt_IcuouILos3turtuCFFIF
然后用字频降序求
ISCTF{so_cLut73r}
Re
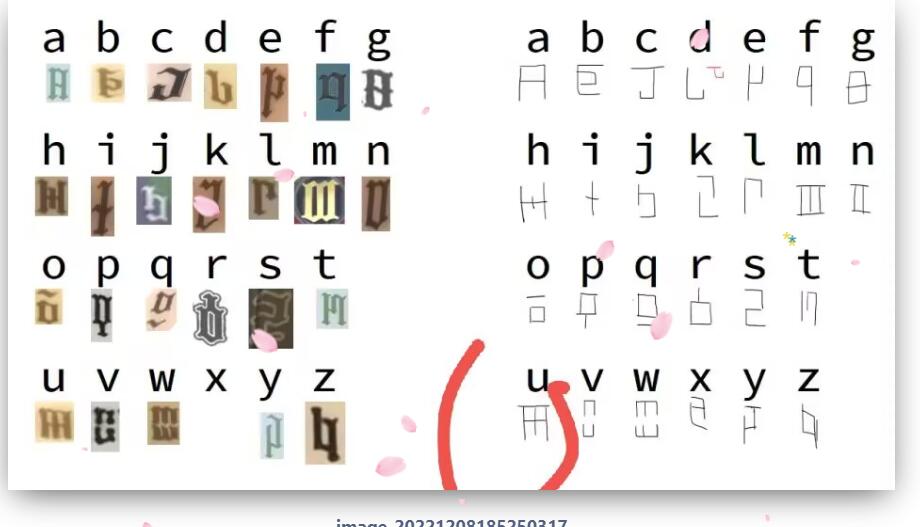
base64
把base64拖进IDA得
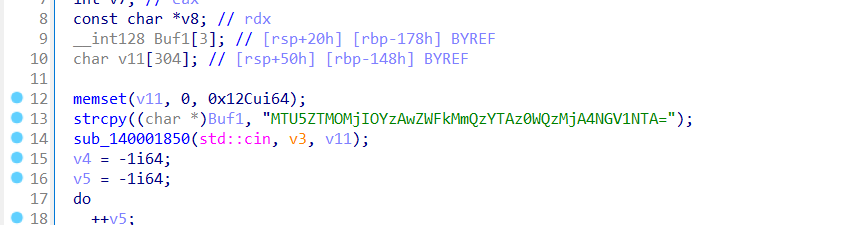
得到一串base64编码
MTU5ZTMOMjIOYzAwZWFkMmQzYTAz0WQzMjA4NGV1NTA=
但是用普通字母表解码得到乱码
然后根据主函数里面的函数找到
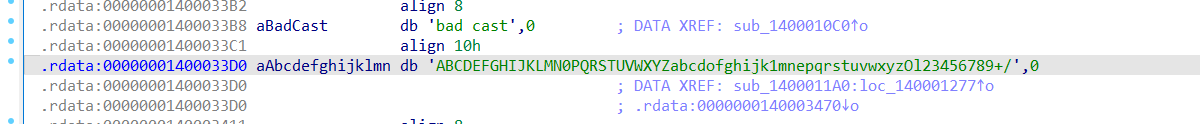
把这个作为base64表解码
ABCDEFGHIJKLMN0PQRSTUVWXYZabcdofghijk1mnepqrstuvwxyzOl23456789+/
脚本
import base64
str_1 = "MTU5ZTMOMjIOYzAwZWFkMmQzYTAz0WQzMjA4NGV1NTA="
str_base = "ABCDEFGHIJKLMN0PQRSTUVWXYZabcdofghijk1mnepqrstuvwxyzOl23456789+/"
str_zh_base = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
flag = base64.b64decode(str_1.translate(str.maketrans(str_base,str_zh_base)))
print(flag)
#159e34224c00ead2d3a039d32084ee50ISCTF{159e34224c00ead2d3a039d32084ee50}
Pwn
nc_pwn
把flag重定向到sh,通过报错输出
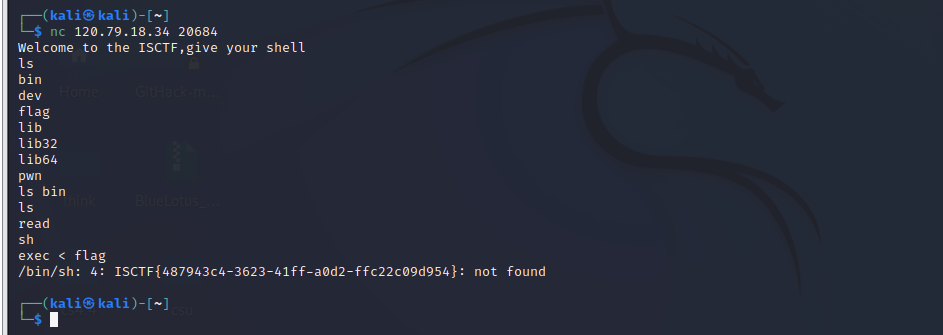
把flag重定向到sh,通过报错输出